Month: January 2026
Blog

How to Choose an Unmetered Bandwidth Dedicated Server
High-traffic services don’t “run out of CPU” first anymore — they run out of network. Internet traffic volume has climbed fast enough that “normal” outbound totals are now measured in exabytes: IBISWorld estimates U.S. internet traffic volume rose from 207.4 exabytes/mo in 2020 to 521.9 exabytes/mo in 2025. That growth changes what good hosting is: you need predictable throughput, not surprise overages or mystery slowdowns.
Choose Melbicom— Unmetered bandwidth plans — 1,300+ ready-to-go servers — 21 DC & 55+ CDN PoPs |
 |
What Factors Matter When Choosing Unlimited Bandwidth Hosting
Picking unlimited bandwidth hosting in 2026 is about guaranteed port speed, network quality, uptime discipline, and transparency. Treat “unlimited” as meaningless unless it’s tied to an explicit unmetered commit (for example, 20 Gbps+) with no hidden caps or throttling. Validate with policy language, test endpoints, and real throughput checks before you migrate production.
Dedicated Server Unmetered Bandwidth vs. “Unlimited” Marketing
The useful term is dedicated server unmetered bandwidth: you’re paying for a fixed-size pipe (1 Gbps, 10 Gbps, 40 Gbps…), and transfer volume isn’t metered. “Unlimited bandwidth” only matters when it’s paired with that explicit pipe size and a provider that can actually deliver it during peak hours.
Two practical reasons this matters:
- Cost predictability: public cloud egress is still usage-priced. Once you’re pushing tens of terabytes per month, outbound transfer alone can land in the “thousands of dollars” range at published list rates. (See the pricing tiers in this public-cloud example.)
- Performance predictability: unmetered bandwidth is a billing term. Performance is still constrained by physics: port speed, congestion, packet loss, and latency.
Which Port Speeds Ensure Reliable High-Traffic Server Performance
Port speed is your ceiling — but only if the provider’s network isn’t oversubscribed and your server can push packets fast enough. In 2026, 10 Gbps unmetered is widely available and often the starting point for serious outbound workloads, while 25/40+ Gbps ports are increasingly common for media, large downloads, and edge-heavy architectures.
Port Speed, Translated Into Monthly Headroom
If you use the connection at full capacity around the clock (uncommon, but helpful for planning), port speed defines your maximum monthly data transfer:
| Port Speed | Theoretical Max Transfer | When It’s the Right Choice |
|---|---|---|
| 1 Gbps | ~324 TB/month | High-traffic web/apps with caching; moderate downloads |
| 10 Gbps | ~3.24 PB/month | Video, software distribution, large API fan-out, “traffic spikes are normal” |
| 40 Gbps | ~12.96 PB/month | Massive content delivery, multi-tenant platforms, sustained burst workloads |
Those numbers are simple math (1 Gbps ≈ 0.125 GB/s). What matters operationally is how close you can get to them during real peak windows.
“Guaranteed” Needs a Definition, Not a Vibe
A modern plan should state, plainly, whether the switch port is dedicated at the advertised speed, how upstream capacity is provisioned for peak periods, and whether any rate-shaping can be applied when you become a “top talker.”
On our dedicated servers page, the language is explicit about “Guaranteed bandwidth, without ratios,” which is exactly the phrasing you want when you’re buying for predictable performance rather than “best effort”.
How to Verify No Hidden Throttling or Caps

A credible “unlimited” plan shows its limits up front: port speed, what direction is unmetered, and what policies trigger intervention. Verify by reading the acceptable-use language, confirming the port is unmetered on egress, and running repeatable throughput and packet-loss tests. If the provider won’t answer clearly, assume throttling exists.
- Force the provider to define “unlimited.” Ask: Is egress unmetered? Is there any soft cap (TB/month), fair-use threshold, or peak-hour shaping? You want a direct answer tied to a stated port speed.
- Look for “ratios,” “fair use,” and “may be limited” clauses. One sentence can turn “unlimited” into “best effort.” If the policy reserves the right to reduce speed after a threshold, treat the plan as capped.
- Test from your side, not theirs. Run sustained transfers at multiple times (especially prime time) and watch for step-function drops that look like shaping. If possible, test with multiple parallel streams; single-stream TCP can under-report capacity.
- Check for measurable packet loss under load. A port can show high Mbps on a short burst while dropping packets on sustained runs. That’s usually upstream congestion, not your server.
- Validate routing transparency. Providers with mature networks publish test endpoints and make it easy to measure path quality. Melbicom’s data center pages include network test downloads per location — useful for sanity-checking throughput before you order.
- Confirm the escape hatch: routing control. If you operate multi-site or carry your own IP space, BGP support is a strong signal of network maturity. Melbicom offers free BGP sessions on dedicated servers, including IPv4/IPv6 and communities, so you can engineer failover and steer traffic instead of hoping for the best.
Network Quality: Redundancy, Peering, and Latency Discipline
Unlimited transfer is worthless if the network collapses under pressure. The hard requirements are boring — and that’s the point.
Redundant switching and routing: Melbicom’s network design describes top-of-rack switches connected to two aggregation switches using vPC and 802.3ad, with L3 redundancy via VRRP — the kind of architecture that turns “a failure” into “a logged event”.
Upstream diversity and exchange presence: Melbicom’s backbone provides 14+ Tbps of capacity with 20+ transit providers and 25+ Internet exchange points (IXPs), which materially improves route options when a carrier has a bad day.
Edge offload for spiky traffic: Even with an unmetered origin port, you don’t want every user request to hit the origin. Melbicom’s CDN spans 55+ PoPs in 36 countries, helping move cacheable traffic closer to users and reducing origin fan-out.
We at Melbicom also support private networking between data centers for east–west traffic, and Melbicom provides S3 object storage to keep bulky objects off your origin servers.
Uptime Is an Engineering Practice, Not a Checkbox
“Uptime” in high-traffic services is rarely about one magic promise; it’s about eliminating single points of failure and shortening recovery loops. A sensible baseline is geography and facility quality: Melbicom hosts servers across 21 Tier III/IV data centers globally with per-server ports up to 200 Gbps — useful when you need to scale throughput without fragmenting your fleet across multiple providers.
Then you look at operational reality: can the provider provision quickly, replace hardware quickly, and answer tickets at 3 a.m. without escalation loops? Melbicom offers 1,300+ ready-to-go server configurations and free 24/7 technical support, so you can scale without waiting on a long procurement cycle. If you need something atypical, we at Melbicom can usually deliver custom configurations in 3–5 business days.
Fast Answers That Prevent Expensive Mistakes
Is “unlimited bandwidth” the same as unmetered? Not automatically. “Unlimited” is only meaningful when it is explicitly tied to an unmetered port speed and a policy that does not introduce fair-use throttling.
Does unmetered always include outbound traffic? No. Some plans only treat inbound as unmetered. If your workload is outbound-heavy, confirm egress is unmetered — in writing.
Will a 10 Gbps port guarantee 10 Gbps of real throughput? Only if the provider can sustain it and your server stack can push it. NIC, CPU packet processing, storage I/O, and TCP tuning can all be bottlenecks.
Dedicated Server Hosting with Unlimited Bandwidth in 2026

A good unlimited-bandwidth plan in 2026 is defined by what it can prove: a stated port speed, a network built for redundancy and low latency, operational uptime discipline, and transparent terms that don’t smuggle in caps. If you’re building for sustained outbound traffic, assume 20 Gbps+ unmetered options are the baseline — and treat every “unlimited” claim as guilty until measured.
- Choose plans with explicit port speeds and written confirmation of egress terms.
- Audit the provider’s network for redundancy, upstream diversity, and peering — then validate with real tests.
- Verify no hidden shaping by running sustained throughput checks during peak hours and watching for packet loss.
- Prioritize providers that offer routing control ( BGP/BYOIP) and edge options (CDN) so you can design around failure, not react to it.
If you do those four things, “unlimited bandwidth” stops being marketing and starts being a dependable part of your capacity plan — the same way you treat CPU cores and storage IOPS. And if you want those characteristics without turning procurement into a guessing game, it helps to start with a provider that publishes network details and makes pre-purchase verification straightforward.
Get unmetered bandwidth you can prove
Spin up 1–40+ Gbps unmetered ports on dedicated servers with global routing, CDN options, and 24/7 support. Validate throughput with test endpoints, then scale confidently.
Get expert support with your services
Blog
Cheap Unlimited-Bandwidth Dedicated Servers: Avoid Hidden Costs
Infrastructure teams running streaming, gaming, AdTech, or analytics workloads know bandwidth—not CPU—is often the real bill driver. Against that backdrop, offers for a cheap dedicated server with unlimited bandwidth are everywhere. The promise is simple: a flat monthly fee, “unlimited” traffic, and instant savings over metered cloud egress. The reality is often less pretty: fair‑use throttling once you actually saturate the port, surprise “abusive usage” emails, or renewal hikes that quietly erase any early discount.
At the same time, the cost of high‑capacity connectivity has collapsed. TeleGeography’s 2025 IP transit data shows that in the most competitive markets, the lowest 100 GigE transit offers sit at about $0.05 per Mbps per month, with 100 GigE port prices falling roughly 12% annually from 2022 to 2025. On the transport side, weighted median 100 Gbps wavelength prices across key routes have dropped 11% per year over the last three years. Those economics are exactly what make genuinely unmetered dedicated servers viable—if the provider actually passes the savings through instead of hiding limits in the fine print.
In other words: the market now supports truly TCO‑optimized unlimited plans, but there are still plenty of traps. The rest of this piece is about telling those apart.
Choose Melbicom— Unmetered bandwidth plans — 1,300+ ready-to-go servers — 21 DC & 55+ CDN PoPs |
 |
What Makes an Unlimited-Bandwidth Dedicated Server Truly TCO-Optimized
A truly TCO‑optimized dedicated server with unlimited bandwidth keeps lifetime cost predictable: “unmetered” with no fair‑use throttling, guaranteed port capacity rather than shared ratios, clear renewal pricing, and enough backbone, peering, and support that you can run hot 24/7 without surprise bills or performance degradation.
- Start with the word “unlimited.” Many offers advertise it but tuck the real terms into a fair‑use policy: you can use as much as you like until the provider decides it’s too much. That usually means throttling or forced plan changes when you actually drive the link near line rate. A cost‑optimized plan instead spells out port speed—1, 10, 40, or even 200 Gbps—and lets you use that capacity continuously. At Melbicom we design our unlimited bandwidth dedicated server plans around that principle: if you pay for a 10 Gbps port, you can run 10 Gbps without being treated as an outlier.
- The second filter is whether the network can support that promise. Melbicom operates a global backbone with 14+ Tbps of capacity, connected to 20+ transit providers and 25+ internet exchange points (IXPs), plus 55+ CDN PoPs that push content closer to users. Ports scale from 1 Gbps up to 200 Gbps per server, so “unlimited” has real headroom rather than marketing‑only numbers.
- Finally, TCO isn’t just bandwidth. Hardware quality, provisioning agility, and support translate directly into operational cost. Melbicom runs 21 global Tier IV & Tier III data centers so you can deploy close to users without redesigning your stack each time. All of that sits behind a flat monthly price per server, with free 24/7 support, so you’re not quietly paying in engineering hours for every incident or hardware tweak.
Which Unlimited Bandwidth Plans Avoid Hidden Renewal Hikes

Unlimited bandwidth plans that genuinely avoid renewal hikes are almost boring: a single, clearly documented monthly price; no “introductory” or “promo” qualifiers; no vague fair‑use clauses; and no essential features split into billable add‑ons after month twelve.
The classic “too good to be true” pattern is a rock‑bottom first‑term price that quietly doubles at renewal. That’s tolerable on a small SaaS plan; it’s disastrous when the asset is a high‑traffic dedicated server with terabytes of data gravity. You migrate workloads, tune performance, maybe colocate other services near it—and then the second‑year invoice jumps 2–3× because the initial rate was promotional. The same trick often shows up as add‑on metering: “unlimited” on paper, but with specific traffic types, locations, or features billed separately.
The way to spot this is to read pricing tables and terms as if you were finance. If the offer page shows only a discounted introductory rate and is silent on renewals, assume the hike exists. If “unlimited” appears alongside mention of 95th‑percentile billing, burst caps, or loosely defined fair‑use policies, the risk is high that your total cost of ownership will drift up as soon as you actually use the bandwidth you’re paying for.
By contrast, a TCO‑oriented unlimited plan aims for rate stability. At Melbicom we price dedicated servers on a flat monthly basis: you pick hardware and port speed, we provide the capacity, and the price tag on our dedicated server page is what you build into your model. If you need more bandwidth, you upgrade the port or add servers—rather than discovering a multiplier in the fine print. The absence of teaser pricing matters because it prevents the infra you depended on at 1× scale from becoming untenable at 10× scale.
How Do Flat-Rate Plans Simplify Bandwidth Budgeting
Flat‑rate unmetered plans simplify bandwidth budgeting by turning a volatile, usage‑driven cost into a fixed monthly line item. Instead of watching per‑GB meters or 95th‑percentile graphs, you decide what a given server and port are worth and know your bill won’t spike every time traffic does.
Usage‑based egress pricing is the opposite. Consider a typical major cloud provider. Public documentation for Amazon EC2, for example, starts data transfer out at $0.09 per GB for the first 10 TB per month, then drops to $0.085 per GB for the next 40 TB and $0.07 per GB for the next 100 TB. Those numbers sound small until you multiply them by real‑world traffic:
| Monthly Data Transfer | Estimated Cloud Egress Cost* | Flat-Rate Server Cost |
|---|---|---|
| 10 TB | ≈ $900 (usage-based) | $500 (fixed) |
| 50 TB | ≈ $4,400 | $500 (fixed) |
| 100 TB | ≈ $7,800 | $500 (fixed) |
*Illustrative calculation based on EC2 data transfer out pricing tiers across the first 150 TB/month. Actual charges vary by region and service.
At small scales, usage‑based billing is manageable. As soon as you cross into tens of terabytes per month, bandwidth becomes your primary cost risk. Analysis from practitioners and vendors alike repeatedly flags data transfer as one of the most common sources of unexpected overruns on cloud bills. That’s before you add AI inference traffic, larger media assets, or new regions.
Flat‑rate unlimited servers invert that risk profile. Instead of bandwidth being a variable cost that explodes with success, it becomes a predictable input: you choose an unlimited bandwidth server with, for example, a 10 Gbps port at a known monthly rate, then treat bandwidth as fixed when you model margins and runway. If you need more capacity, you add nodes or step up port speeds, but individual traffic spikes don’t translate into four‑ or five‑figure surprises. Pair that with a globally distributed CDN—and you can keep content close to users while keeping origin bandwidth and cost curves stable.
From a planning perspective, that means fewer worst‑case scenarios in your spreadsheets and more confidence in long‑term commitments. Bandwidth becomes the boring part of your infrastructure P&L—which is exactly what most CFOs and CTOs want.
From Chasing a Cheap Unlimited Bandwidth Plan to Choosing a TCO-Optimized One
The current market makes it easy to chase the absolute lowest sticker price on anything labeled “unlimited.” The problem is that infrastructure rarely stays at its day‑one footprint. If your workloads grow as intended, 10× traffic is a matter of when, not if—and contracts that looked cheap at small scale can quietly accumulate risk.
What you want instead is a TCO‑optimized unlimited bandwidth strategy: understand how much bandwidth your workloads will consume, pick flat‑rate plans that genuinely let you use the ports you’re paying for, and ensure the underlying network and support model can keep up without hidden surcharges. Unlimited bandwidth dedicated servers that meet those requirements let you absorb new features, bitrates, codecs, and even extra regions without having to renegotiate your relationship with finance every quarter.
When you zoom out from individual offers, a few practical recommendations emerge:
- Treat “unlimited” as a technical claim, not a slogan. Ask explicitly what happens if you run the port hot 24/7. If the answer involves undefined “fair use,” thresholds, or 95th‑percentile clauses, assume there are financial or performance cliffs.
- Model renewals/edge cases before you sign. TCO‑optimized plans make renewal pricing explicit and avoid jumps after an introductory term. Include high‑traffic months, peak events, and feature launches in your cost scenarios—not just your current baseline.
- Move bandwidth from variable to fixed where it makes sense. For workloads pushing tens of terabytes per month, flat‑rate unmetered plans plus CDN offload are often cheaper and vastly more predictable than per‑GB egress, even if the per‑server sticker price looks higher at first glance.
- Favor providers that invest in backbone capacity and peering. Multi‑terabit backbones, 20+ TP, and broad IXP reach reduce both performance risk and the chance that your “unlimited” plan is really just oversold capacity with contention during peaks.
In practice, you’ll mix models—some usage‑based services where traffic is low or bursty, some flat‑rate unmetered infrastructure where throughput dominates. The key is that you choose where to take risk, instead of letting unclear fair‑use rules decide for you.
Choose flat-rate unlimited bandwidth servers
Predictable pricing and performance without fair-use throttling. Deploy in 21+ global locations with ports up to 200 Gbps and 24/7 support. Pick hardware and port speed, and keep bandwidth a fixed monthly cost.
Get expert support with your services
Blog
Compliance Playbook For Italian Dedicated Servers
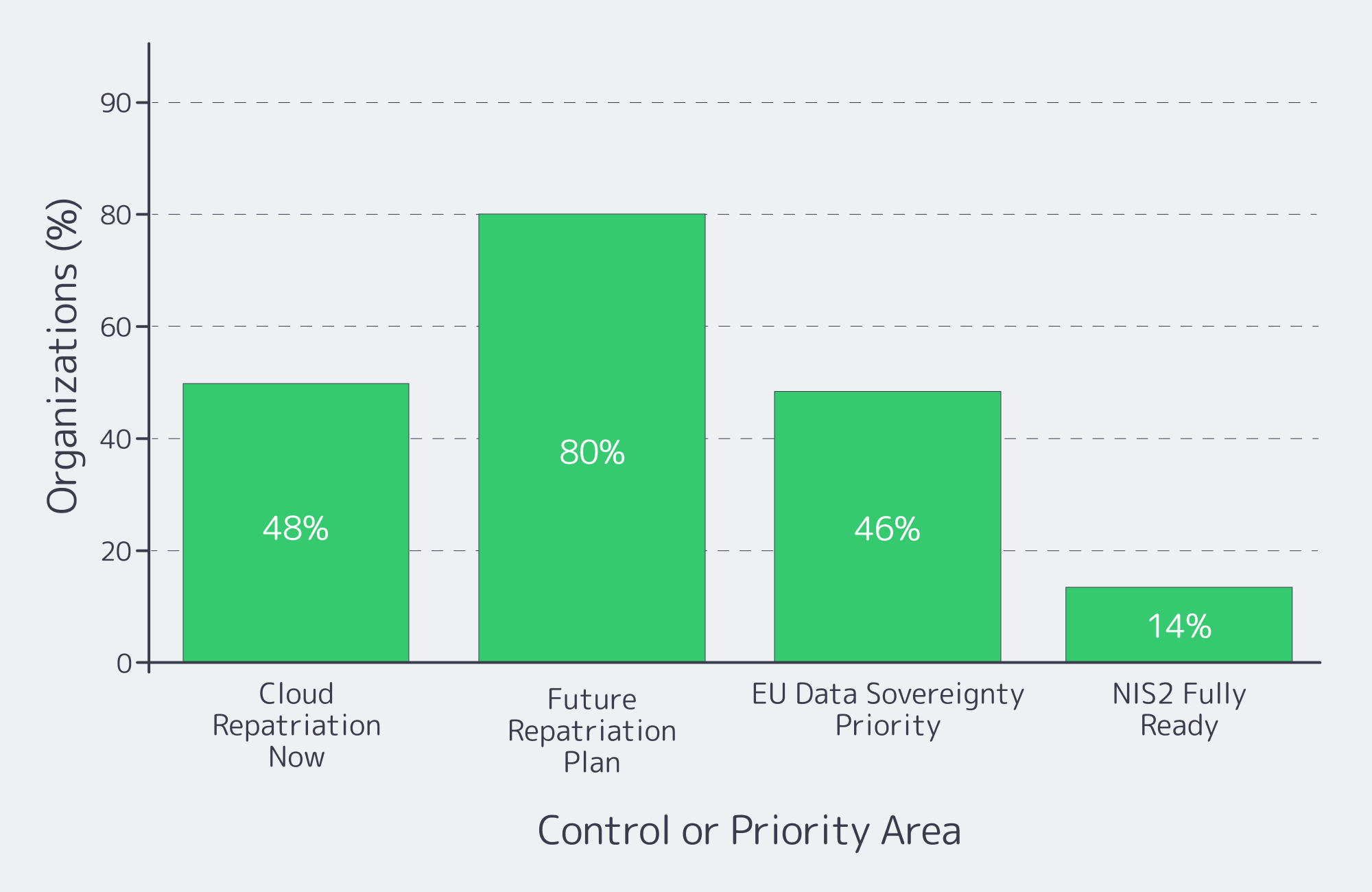
European regulation has quietly killed “move fast and break things” for infrastructure teams. GDPR set the baseline for data protection; NIS2 and DORA now turn cyber‑risk and resilience into board‑level issues. Recent research shows that over 48% of companies are considering or actively moving workloads from public clouds back on‑premises or to private clouds, and around 80% expect to repatriate some workloads within the next two years, largely due to cost and sovereignty pressures.
At the same time, 46% of European security leaders now rate EU data sovereignty as their single most important buying criterion, ahead of cost. For regulated services, that translates into a blunt infrastructure mandate: keep critical data on infrastructure where you can prove where it lives, who can access it, and which controls wrap around it.
Italy is a strong candidate for that anchor point. Palermo sits on top of multiple Mediterranean cable landing stations, and Melbicom’s Tier III data center there connects directly into those systems. That location can shave 15–35 ms of latency to North Africa and the Middle East and improve overall route quality by 50–80% for those regions. For EU‑facing workloads, hosting on a dedicated server in Italy combines clear EU jurisdiction with low‑latency connectivity into European backbones.
Choose Melbicom— Tier III-certified Palermo DC — Dozens of ready-to-go servers — 55+ PoP CDN across 36 countries |
 |
This article offers a practical compliance playbook for running regulated workloads on a dedicated server in Italy deployment – how to map data flows, what GDPR artifacts to demand, which controls line up with NIS2 and DORA, and how to stay audit‑ready instead of scrambling when someone says, “We have an assessment next month.”
What GDPR Artifacts to Request from Italian Dedicated Server Hosting Providers
For Italian hosting, you want GDPR paperwork that proves where data lives, who touches it, and how it’s protected. In practice, that means a DPA with teeth, full sub‑processor and location transparency, mapped data flows, security certifications or audits, and clear incident‑handling clauses you can point to in an assessment.
The non‑negotiables:
- Data Processing Agreement (DPA). Your DPA with a hosting provider should clearly scope which services are in play, what security measures apply, how data‑subject rights are supported, and how audits or inspections can be performed.
- Sub‑processor and location transparency. Demand a current list of sub‑processors with their roles and countries.
- Data‑flow and data‑category mapping. Before migrating, map which components on the server handle personal data, which handle telemetry or logs, and which external services receive copies (backups, monitoring, email gateways). That map becomes your single reference when customers or regulators ask, “Exactly where does this field go?”
- Security certifications and audits. Independent audits are now standard proof that “appropriate technical and organisational measures” exist.
- Incident handling and cooperation clauses. Your DPA and main contract should commit the provider to prompt incident notification and meaningful cooperation (log access, forensic details, timelines) so you can meet GDPR’s breach‑reporting deadlines and NIS2/DORA thresholds without conflict.
With this pack in place, you can show regulators and enterprise customers that server hosting in Italia isn’t just a rack in Palermo – it’s a controlled processing environment with clear legal responsibilities and traceable data flows.
Which Security Controls Meet NIS2 and DORA Requirements
NIS2 and DORA effectively codify what used to be optional security hygiene. On a dedicated server in Italy, regulators expect encrypted data, strong identity and access control, rich logging and monitoring, disciplined patching, and tested incident‑response – plus contracts that make your provider an accountable part of that control system.
Encryption, Access, & IAM for Server Hosting Italia
Encrypt data at rest and in transit by default: full‑disk or volume encryption for storage, TLS for services, and VPN or private links for management and inter‑DC traffic. NIS2 guidance calls for “state of the art” cryptography and documented key‑management, including rotation and logging. Combine that with strong identity: SSH keys or certificates for server logins, MFA on Melbicom’s control panel and IP‑KVM, and role‑based access control so only those who truly need it can touch production.
Logging, Monitoring, & Vulnerability Management
NIS2 and DORA both assume that you can detect, investigate, and reconstruct incidents. Centralize system, application, database, and network logs from your Italian server into a SIEM or log pipeline, define retention windows, and monitor for anomalies. Only 14% of organizations say they’re fully NIS2‑ready, according to IDC research sponsored by Microsoft – most are still filling gaps in monitoring and response. A disciplined patch and vulnerability‑management process – defined patch windows, regular updates, and documented remediation timelines for critical CVEs – is one of the fastest ways to close that readiness gap.
Incident Response and Resilience on Your Server Italia Stack
NIS2 and DORA introduce strict timelines and expectations for incident reporting, alongside resilience requirements. Essential entities under NIS2 face fines of up to €10 million or 2% of worldwide annual turnover, whichever is higher, if they fall short on key security obligations. To keep your Italian server environment on the right side of that line, you need a written incident‑response plan, mapped roles between your team and Melbicom, and a tested disaster‑recovery design: encrypted backups (for example, to Melbicom’s EU‑based S3 object storage in Amsterdam), restore drills, and, where needed, second‑site capacity in another EU DC.
How GDPR, NIS2, and DORA Line Up for Hosting
| Framework | Primary Focus | Hosting‑Relevant Must‑Haves |
|---|---|---|
| GDPR | Personal‑data protection and privacy | DPA with your Italian provider; transparent data flows and sub‑processors; appropriate security (encryption, access control); breach detection and 72‑hour reporting processes. |
| NIS2 | Cybersecurity for essential/important entities | “State of the art” controls: encryption, MFA, logging/monitoring, vulnerability management, documented risk management, and fast incident reporting backed by clear governance. |
| DORA | Digital operational resilience for finance | ICT‑risk framework, segregated and tested backups, documented RTO/RPO, rigorous incident handling and reporting, and strong third‑party oversight for infrastructure providers. |
How to Ensure Audit Readiness for Italian Dedicated Hosting
Audit readiness for Italian hosting means treating your environment as an evidence machine, not just a stack of servers. You need up‑to‑date documentation, log trails you can reconstruct incidents from, clear ownership with your provider, and a lightweight review cadence that keeps controls aligned with GDPR, NIS2, and DORA expectations.
Start with an evidence repository. Collect the DPA, main contract, network diagrams, data‑flow maps, and risk assessments that describe your Italian environment. Add vulnerability‑scan reports, backup/restore test logs, penetration‑test summaries, and configs proving MFA, encryption, and hardening. When an audit lands, you’re curating from a library, not hunting through inboxes.
Then audit from the outside‑in. Periodically run an internal checklist against GDPR, NIS2, and DORA requirements: Can you show where personal data sits on your dedicated server Italy deployment? Produce a sub‑processor list? Prove that backups are tested? The point isn’t to build a bureaucracy – it’s to ensure that if a bank client, regulator, or board asks, you have concrete answers backed by evidence.
Finally, stay ahead of regulatory drift. GDPR enforcement has already produced roughly €5.88 billion in cumulative fines as of early 2025, and regulators are widening their target list beyond “big tech.” NIS2 and DORA are only increasing the stakes. Build a lightweight governance loop: periodic reviews of guidance from EU and Italian authorities, internal gap analyses, and scheduled updates to your controls and documentation. When rules shift, you adjust the Italian environment deliberately instead of reacting under audit pressure.
Turning a Dedicated Server in Italy Into a Compliance Advantage
Put all of this together and a dedicated server in Italy stops being “just hosting” and becomes part of your governance architecture. You concentrate your regulated workloads in a single‑tenant, clearly located environment under EU law; you can prove where every packet lives, who has access, and which controls wrap around it.
Key Takeaways for Hosting in Italy
- Anchor sensitive workloads in a single‑tenant Italian environment. Keep personal‑data‑heavy systems on a dedicated server Italy deployment so you can explain data residency and access in one slide – and avoid cross‑border transfer issues unless they’re explicitly required and documented.
- Treat security controls as regulatory requirements, not best‑effort. Map encryption, MFA, logging, vulnerability management, backups, and incident response directly to GDPR, NIS2, and DORA articles. Make sure each control has an owner, a test schedule, and an associated piece of evidence.
- Build audit readiness into day‑to‑day operations. Maintain an evidence repository, standardize log retention, and schedule periodic “mini‑audits” so there are no surprises when an external assessor or major customer wants proof that your Italian hosting stack is under control.
Get compliant hosting in Italy
Deploy dedicated servers in Palermo with EU data residency, NIS2-ready controls, encrypted backups, and 24/7 support. Choose a configuration that fits your workloads and compliance goals.
Get expert support with your services
Blog
Italy Dedicated Servers: A Due Diligence Playbook
Italy is no longer a “secondary” EU hosting decision. Market researchers estimate the country’s data‑center market at about $5.73B and project it to reach $7.54B in the near term, with forecasts climbing to $13.49B by the end of the decade.
If you’re here to rent a dedicated server in Italy, treat this guide like a production dependency: translate workload into CPU/RAM/NVMe and bandwidth tiers, pick a city that hits latency targets, and validate the boring‑but‑fatal details—routing, out‑of‑band access, remote hands, provisioning, and exit clauses. This is the checklist you can reuse.
Choose Melbicom— Tier III-certified Palermo DC — Dozens of ready-to-go servers — 55+ PoP CDN across 36 countries |
 |
Italy: Rent a Dedicated Server by Sizing the Workload First
Sizing isn’t about buying “big.” It’s about making performance predictable under ugly realities: cache misses, replication spikes, batch jobs colliding with user traffic, and the day your database vacuum decides it’s the main character.
- Profile (peak QPS, background jobs, read/write mix, hot‑set size).
- Translate into CPU/RAM/NVMe and a baseline bandwidth tier.
- Add headroom you can justify (incident mode + growth).
- Decide scaling path (vertical now, horizontal later—or vice versa).
Dedicated server Italy CPU: map concurrency to cores and clocks
For latency‑sensitive services, clock speed and sustained all‑core behavior often matter more than “how many cores can we afford.” Ask for the exact CPU model and generation, then sanity‑check it against your p95 CPU time per request and expected concurrency. If the provider can’t name the SKU, you can’t reproduce performance later.
RAM: budget for churn, not average
Memory pressure is an incident generator. Size for the worst five minutes: GC churn, cache turnover, and page cache behavior during heavy reads. Confirm ECC RAM and ask how upgrades are handled (in‑place vs reprovision). For data stores, treat RAM as a performance tier (indexes + hot sets), not a cost center.
Storage: NVMe as the default, not the upsell
NVMe isn’t just “faster disk.” It’s a different latency profile. NVM Express’ analysis notes that PCIe 4.0 x4 NVMe can be over 10× faster than SATA 3.0 at the interface level, and cites lab results showing ~5.45× more read bandwidth and ~5.88× more random‑read IOPS for data‑center NVMe versus enterprise SATA. If storage touches your request path, NVMe is how you buy predictability.
Bandwidth: tier it like a resource, not a line item
Define two requirements: steady‑state commit (normal egress, replication) and burst (backfills, re‑shards, release windows). Also decide if you need metered transfer or an unmetered port. The “right” tier is the one that doesn’t punish growth—or turn incident response into a cost spike.
Which Italian Data Centers Meet Low-Latency EU Requirements
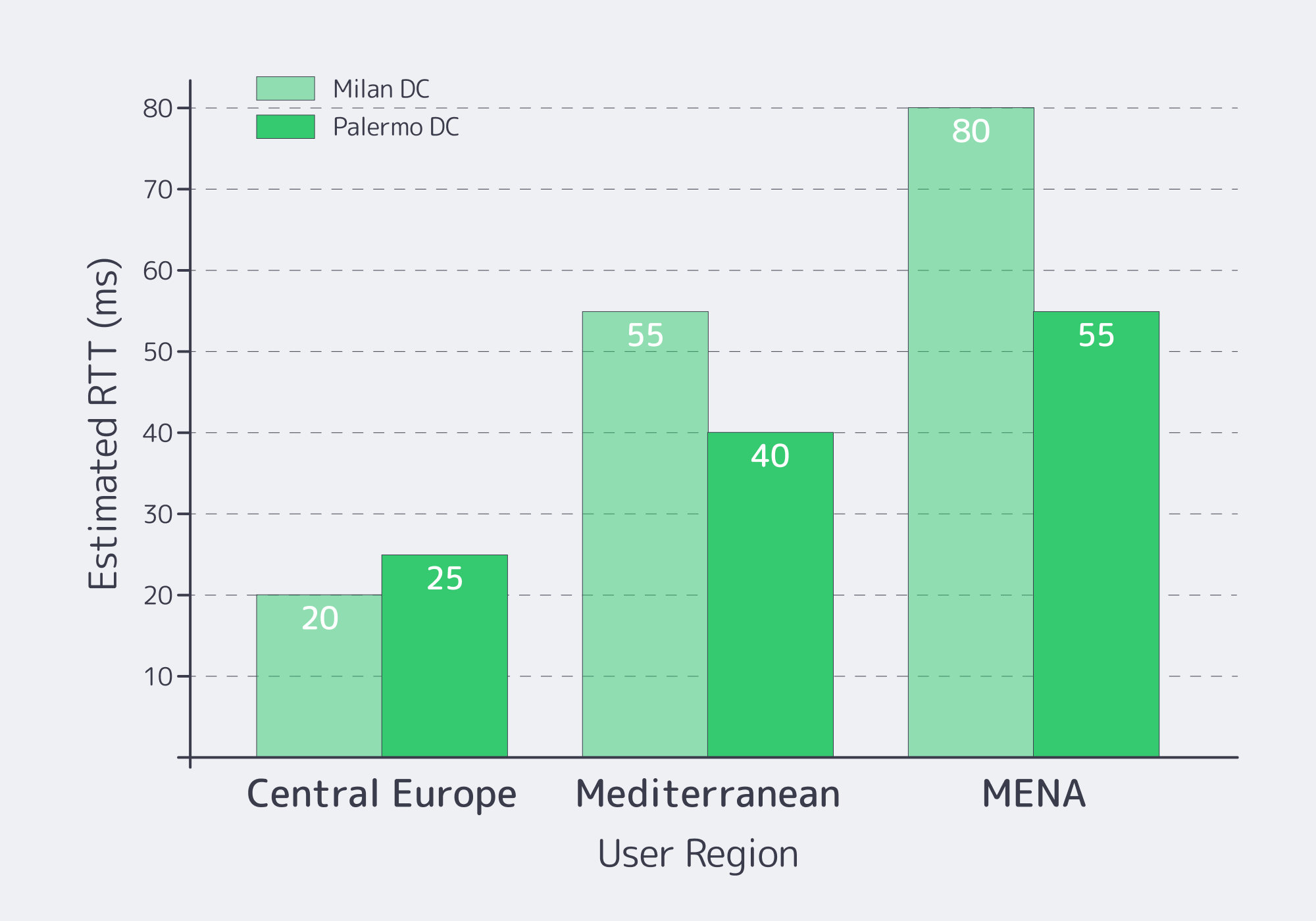
Italy meets low‑latency EU requirements when you choose the city for your user geography and upstream routes—not because “Italy is central.” Milan is typically best for Central/Northern Europe paths; Southern Italy can be better for Mediterranean and MENA adjacency. Validate with real RTT and loss measurements from your top regions, then pick what hits your p95 SLOs.
Start with targets, then back into geography. A public ping dataset shows Milan ↔ Frankfurt round‑trip latency around ~10.3 ms under typical conditions. That’s why Milan is the default “close to everything” choice for many EU workloads.
But “Italy” is not just Milan.
Palermo as a latency and routing lever
Melbicom’s Italy location is Palermo, a Tier III facility with 1–40 Gbps per server options. The Palermo site is much closer to Mediterranean cable landings and can save 15–35 ms of latency and deliver a 50%–80% overall quality improvement for traffic tied to Africa, the Mediterranean, and the Middle East.
Due‑diligence move: don’t accept “quality” as a vibe. Run multi‑probe RTT + packet‑loss checks from the networks you care about.
What to Validate in Italian Hosting MSAs
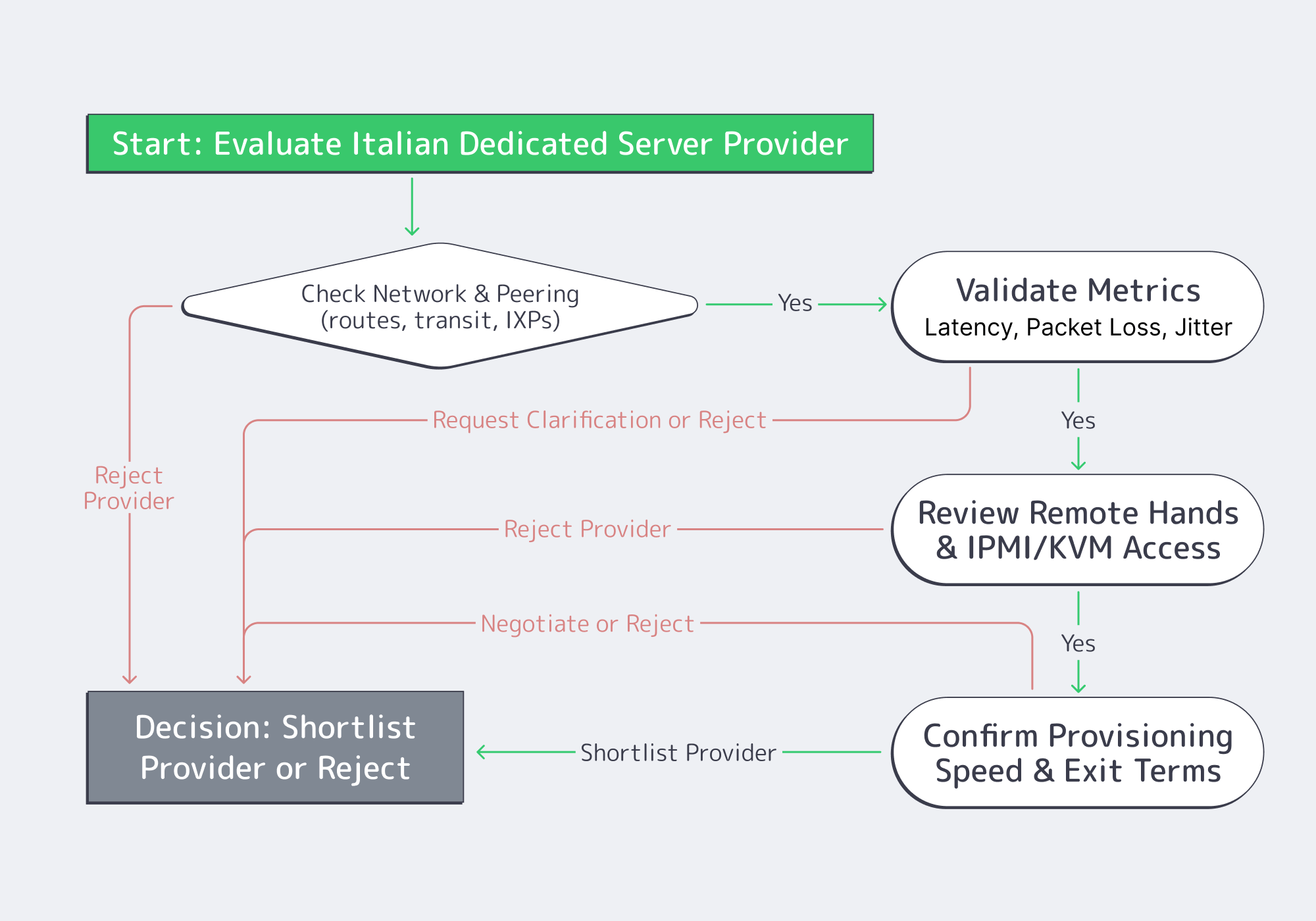
Treat the SLA (or MSA + service terms) like part of your architecture: it defines how performance is measured, how fast issues are handled, and what “support” actually includes. Validate peering quality, packet‑loss targets and measurement windows, remote‑hands scope, IPMI/KVM access, provisioning timelines, and exit/migration clauses. Anything ambiguous becomes a problem during an outage.
Here’s the due‑diligence checklist that actually changes outcomes.
- Peering and routing evidence. Ask for traceroutes to your top destinations (or a looking‑glass), and verify paths stay sane during peak hours. “Many peers” is not a guarantee; consistent paths are.
- Packet‑loss targets + measurement method. A common backbone benchmark is ≤0.1% average monthly packet loss—but only if the agreement defines where and how it’s measured. Lock down scope (inside provider backbone vs public internet), sampling, and how you can reproduce the metric.
- Remote hands scope. Define what’s included (reboots, reseats, KVM hookup) vs billable (disk swaps, rack work), plus response times and escalation. This is how you turn “we’ll help” into an operational control.
- IPMI/KVM access (out‑of‑band recovery). Out‑of‑band access is your last line of defense when the OS is dead or the network is misconfigured. Validate isolation, credential rotation, and auditability.
- Provisioning lead time (stock vs custom). Put timelines in writing and separate “stocked config activation” from “custom build delivery.” When you need capacity under pressure, hand‑wavy provisioning is not a plan.
- Exit and migration clauses. Confirm notice periods, data wipe proof, and IP handling. If IP identity matters, routing options can make migrations cleaner; Melbicom supports BYOIP and BGP sessions on dedicated servers.
How to Build a Server Scoring Matrix
A scoring matrix turns subjective impressions into a repeatable decision. Weight the criteria that map to production risk, score each provider only with evidence, and force trade‑offs into the open. Include workload fit, measured latency, network quality, operational access (IPMI/KVM, remote hands), provisioning, and exit terms.
Weighted Score = Σ (weight_i × score_i) / Σ weight_i # score_i is 1–5, backed by a test result or a contract clause |
| Category | Weight (%) | What “5/5” looks like |
|---|---|---|
| Workload fit (CPU/RAM/NVMe) | 25 | Exact CPU SKU, ECC RAM, NVMe options; clear upgrade path |
| Latency to users/partners | 20 | Measured RTT meets p95 SLO from target regions |
| Network & peering quality | 20 | Clean traceroutes; defined loss target + measurement method |
| Operations (IPMI/KVM + support) | 20 | OOB access works; remote‑hands scope + escalation is explicit |
| Provisioning + exit terms | 15 | Timelines in writing; migration window; IP portability options |
To score honestly: run the same tests from the same probes, mark unknowns as unknowns, and penalize ambiguity in service terms. Evidence beats vibes.
Frequently Asked Questions (Ops Edition)
Is “Italy” automatically the lowest‑latency EU option? No. Latency is route‑dependent. Italy can be excellent for specific corridors, but you need measurements from your user regions and partner networks.
What’s the minimum due diligence before signing? A test IP for RTT/loss, exact hardware SKUs, written provisioning commitments, remote‑hands scope, and an exit clause you can execute without downtime gambling.
Do I need a CDN if I rent a dedicated server in Italy? If you serve global users or heavy static content, a CDN is how you stabilize TTFB and reduce origin egress. Melbicom delivers CDN capacity through 55+ PoPs in 36 countries.
What’s the safest way to migrate in? Parallel run: replicate continuously, cut over in stages, and keep rollback. If stable IP identity matters, consider BYOIP via BGP sessions.
Key Takeaways for Renting a Dedicated Server in Italy
- Size from workload behavior: CPU/RAM/NVMe and bandwidth tiers should map to measurements, not guesses.
- Pick Italian locations by latency targets and real routes—then verify with RTT and packet‑loss tests.
- Treat peering quality and out‑of‑band access as production requirements.
- Put remote hands, provisioning, and escalation rules in writing.
- Build an exit plan: migration windows and IP strategy are operational safety nets.
Conclusion: a Dedicated Server Is an Architecture Decision
An Italy dedicated server is only “fast” if the whole stack is predictable: hardware that matches the workload, geography that matches users, routing that stays sane, and service terms that make recovery and exit possible. Do the diligence once—profile, measure, and score—and procurement becomes repeatable instead of emotional.
Deploy in Palermo today
Stocked servers activate within 2 hours; custom builds ship in 3–5 days. Compare Palermo vs Milan for your latency targets and run real tests before ordering.