Month: July 2025
Blog
File Server Backup Solutions: Step‐by‐Step Protection
Modern data protection has evolved far beyond manual copy scripts; the stop-gap era is well and truly gone. Over the years, data estates have sprawled across petabytes, the backups have become the prime target of attacks, and modern compliance demands are stricter than ever before, driving real changes in the way that file server admins protect data for provable recovery.
Where once techs were occupied after-hours, swapping disks with little more than a prayer that cron jobs ran smoothly, they now need provable safeguards driven by evidence and immutable data restoration.
So to prevent budgets spiraling and redundant copies, we have put together this guide to walk you through five interlocking steps to ensure that file server failure or ransomware blasts don’t leave you in crisis. They are: classification, granular retention, automated incremental snapshots, restore testing, and anomaly-driven monitoring. If followed strategically hand in hand with the following technologies: Volume Shadow Copy snapshots, immutable object storage, and API-first alerting, then you have a fool-proof restore process for whatever you may face.
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Share Classification: How to Prioritize
Backup windows become bloated when every share is treated equally, and that is a sure path to unmet Recovery Point Objectives (RPOs). Therefore, your first step should be a data-classification sweep to categorize data into the following tiers:
- Tier 1 – Business-critical data such as finance ledgers, deal folders, and engineering release artifacts.
- Tier 2 – Important but not critical data from department workspaces and any ongoing project roots.
- Tier 3 – Non-critical archives and reference libraries data, project dumps that are at the end of life.
Classifying data in this manner drives everything downstream. Be sure to interview data owners, scan for regulated content (PII, PHI), and log the operational impact of losing each share. This helps with creating policies; the data protection needs of a finance ledger that changes every hour are different from those of an archive with quarterly updates.
The approach also ties hand in hand with demonstrating that you are accomplishing compliance demands, such as the GDPR mandate that states at-risk EU personal data must have adequate safeguards, thus preventing fines.
Granular, Immutable Retention Policies
With the tiers clarified, you can begin to craft retention that reflects data value and change rate. The typical “backup daily, retain 30 days” blanket rule hogs space unnecessarily, and critical RPO targets may still fall through the cracks with this method. Using a tiered matrix ensures efficient protection, keeping things sharp without wasting storage. Take a look at the following example:
| Tier | Backup cadence | Version retention |
|---|---|---|
| 1 | Hourly incremental snapshot and nightly full | 90 days |
| 2 | Nightly incremental snapshot and weekly full | 30 days |
| 3 | Weekly full | 14 days |
Non-negotiable Immutability
Worryingly, in 97% of ransomware incidents, the attackers corrupt backups directly, making immutability vital.[1] Using WORM-locked object storage, be it S3-Object Lock, SFTP-WORM appliances, or cloud cold tiers for snapshots, means killswitch attempts fail. One simple change, which takes away a ransomware gang’s power, is to have one recent full backup for every Tier 1 dataset stored in an immutable bucket for 90 days before aging out automatically. That way, a “pay or lose everything” threat is of no concern.
Following the 3-2-1 pattern (three copies, in two media, one kept off-site) helps reinforce disaster resilience. So, be sure to ship nightly copies of Tier 1 critical data and weekly copies of Tier 2 important data to remotely located storage in a different region. Remember, latency is less important than clean data should a physical disaster, such as a site-level fire or flood, happen to occur.
Tools for Automating Incremental Snapshots: VSS/LVM/ZFS
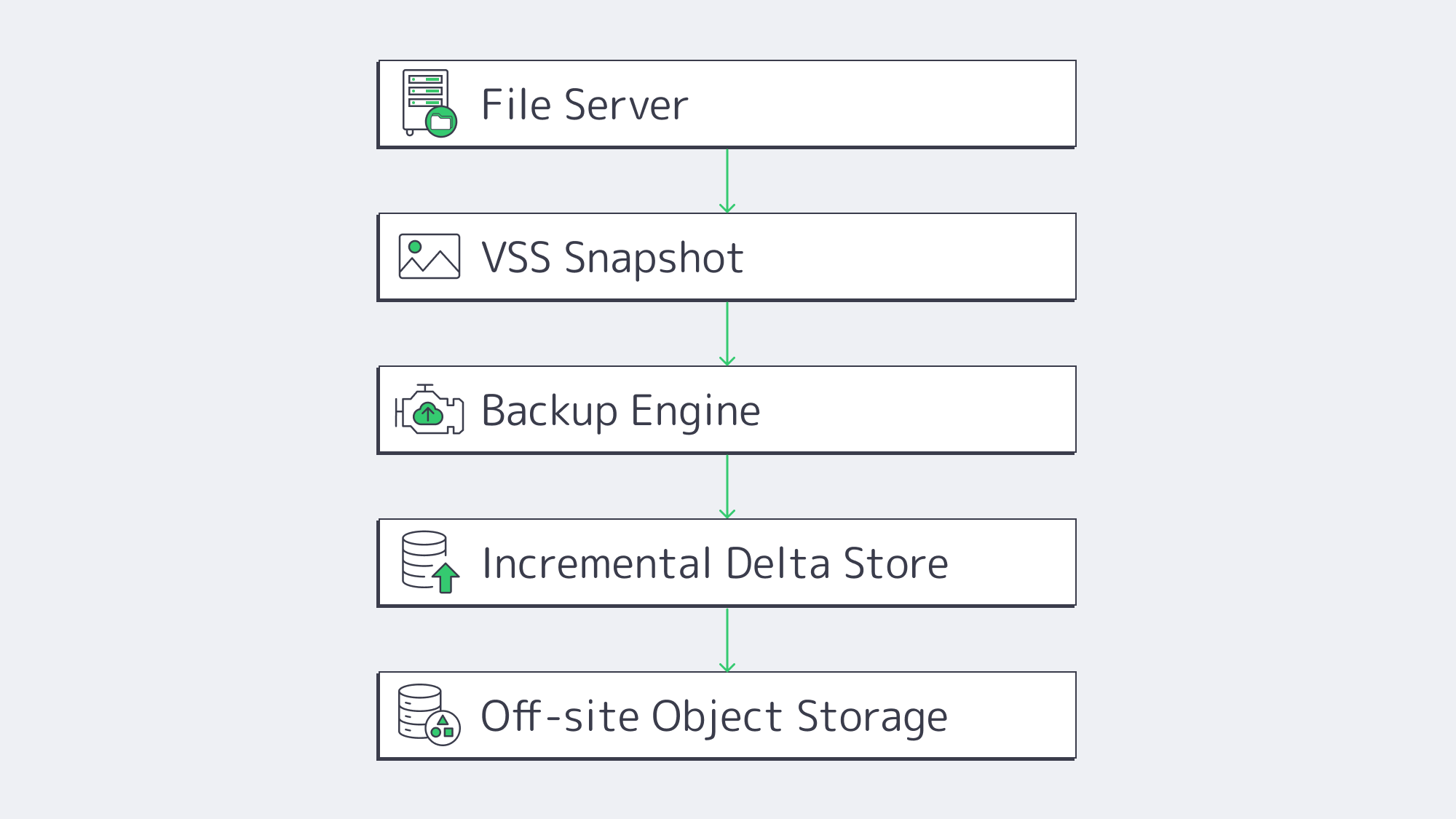
Modern backup solutions have moved away from running full multi-terabyte volumes all weekend, favoring synthetic incremental snapshots. Now, following an initial full seed, only deltas move. This can cut backup traffic and runtime by as much as 80–95 %[2], allowing continuous protection without crushing the network, courtesy of the smaller payloads.
Automating the process requires no human intervention:
- Job schedulers can be automated to fire according to the tier classification (hourly, nightly, etc).
- Post-process hooks immediately replicate backups to off-site targets.
- Report APIs automatically push status to Slack or PagerDuty.
The automated filesystem snapshots run in an application-consistent state, ensuring zero downtime, and they also eliminate “file locked” errors. If using Volume Shadow Copy Service (VSS) for snapshot automation on Windows, there is a momentary freeze as it writes, and the backup software captures point-in-time blocks without downtime, regardless of the file type, even open PSTs or SQLite files are instantly written. The same can be said for Linux-equivalent software such as LVM snapshots or ZFS send/receive.
Testing Restores for Real-World Recovery Before the Fact
Almost 60 % of real-world recoveries fail for one of the following reasons: corrupt media, missing credentials, or mis-scoped jobs.[3] Each of these risks can be reduced by testing restores for real-world situations by simply baking restores into the run-book and making it a part of regular operations. We suggest the following:
- Weekly random spot checks: pick three files from a variety of tiers; restore them to an isolated sandbox and validate hashes.
- Quarterly full volume recovery drills: Using a new VM or dedicated server host, perform a full Tier 1 recovery. Be sure to time the process and log any gaps identified.
- Verification after any changes: Ad-hoc restore tests should be performed following any changes, such as new shares being added, tweaks to ACLs, or backup agent upgrades
Remember, while the auto-mount VM features included in many modern suites are useful to verify boot or run block-level checksums following a backup, human-eyed drills are still needed to validate run-books and credentials. Double-checking manually also builds muscle memory for when teams are under stress.
Anomaly Monitoring and Wiring Alerts into Operational Fabric
Automation has its perks, but monitoring is essential. Ransomware encrypts at machine speeds, and so a quiet backup that finishes without alert could be masking a future disaster, and you won’t know until the next scheduled backup. Anomaly engines can help observe backup activity and watch for spikes or changes in compression ratios and file counts to spot deletion and make sure delta ballooning is identified efficiently. If your nightly capture is usually around 800MB, and last night’s job hit 25 GB, time is of the essence. Next week’s review will be too late.
Back-end metrics also need monitoring for red flags such as low repository disk capacity, climbs in replication lag, and immutable lock misconfigurations. API endpoints or webhooks, fed to SIEM, Prometheus, or similar, can help with vigilance, and any failures can be reported to teams with a one-line cURL script; for example, JSON payloads triggering auto-ticket creation. Restrict the triggers to actionable events (failed jobs, anomalies, capacity thresholds) to prevent alert fatigue and be sure to train on them.
By integrating anomaly-driven monitoring into daily ops, you turn your backups into a built-in early-warning radar, and given that 97 % of ransomware strains seek backup repositories first [4] you will be in a good position to catch attack vectors within minutes. That way, you can stop encryption in its tracks and isolate infected shares effectively, preventing downtime and business crises.
Modern Data Protection: a Continuous Process, Not a Product
A disciplined process is needed for file-server protection in the modern world. It starts with classifying shares to make sure resources flow efficiently, then granular immutable retention can be put in place, assisted by technology such as VSS or similar for snapshot automation. Rehearsing restores turns the process into muscle memory, as does making anomaly alerts an integral part of everyday operations, reducing the level of panic faced during a real crisis.
Though the steps alone are each modest, they work in conjunction to form a last-line defense that hardens backups sufficiently to survive ransomware, hardware fires, and accidental deletes. The results of following the outline shared are quantifiable, too. 21 days is considered an industry-average following a ransomware outage,[4] but this recovery window shrinks to merely hours under testing, with clean infrastructure housing immutable backups at the ready.
Deploy Your Backup Node Now
Get a dedicated server configured as a backup node within 2 hours. Immutable storage, high-bandwidth links, and 24/7 support.
Get expert support with your services
Blog
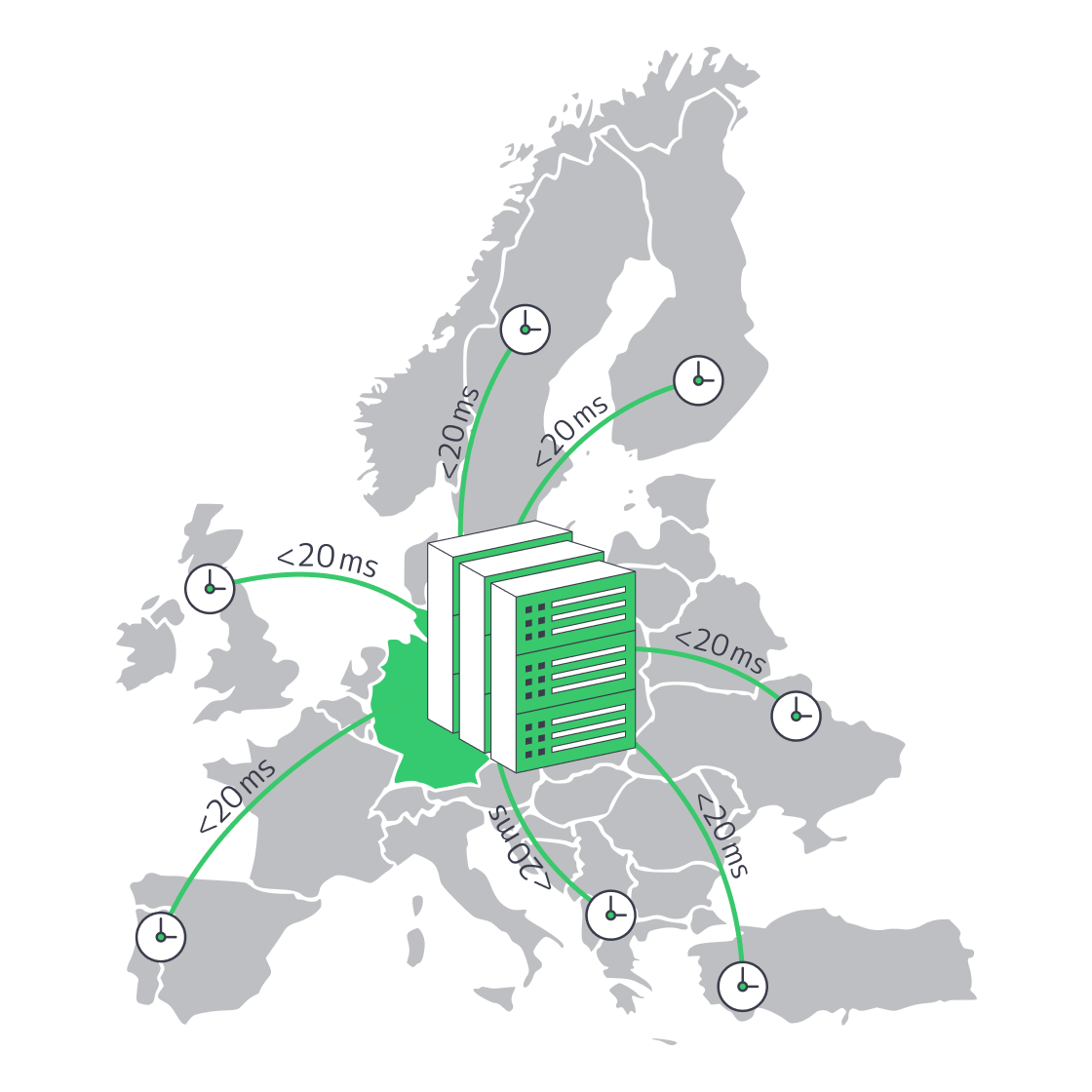
Germany’s Servers Blend Savings With Low Latency
The German hosting sector has been developing rapidly to become the default hosting location for startups with limited budgets that must meet enterprise-level performance metrics. Frankfurt is the ecosystem’s center of gravity; it hosts DE-CIX, the most active internet exchange point in the world, along with a concentration of Tier III+ data centers that guarantee a round-trip time of under 20 ms to most major European capital cities. Competition is intense and hardware is getting aggressive, coupled with burstable 95th percentile bandwidth plans and requirements to be efficient globally. This is indeed a challenge to keep up with: by reducing the TCO, with no loss of speed, resiliency, or scale.
Choose Melbicom— 240+ ready-to-go server configs — Tier III-certified DC in Frankfurt — 55+ PoP CDN across 6 continents |
 |
Why a Cheap Dedicated Server in Germany Still Delivers Enterprise Muscle
Server pricing in Germany is based on the economics of supply and demand. Frankfurt alone exceeds 700 MW of installed IT power, second in Europe only to London, with vacancy rates just under 7 percent, which is forcing providers to sharpen their pricing strategies.[1] Industry veterans on WebHostingTalk have long observed that “Germany is actually the cheapest place in Europe to buy a dedicated server”[2] as compared to the U.S. coastal cities, where land, labor, and power costs are driving up monthly costs.
Competition shows up on invoice line items:
| Spec | Typical Monthly Price | Note |
|---|---|---|
| 8-core Xeon / 32 GB / 1 Gbps | €110–€140 | Port usually unmetered at 1 Gbps |
| 16-core EPYC / 64 GB / 10 Gbps | €220–€280 | Burstable to 20 Gbps on 95th-percentile |
| 32-core EPYC / 128 GB / 25 Gbps | €450–€550 | High-frequency trading & AI edge |
The second cost lever is flexible burstable billing. Most German operators bill on the 95th percentile, allowing customers to exceed their commitment by two or three times in the short run without penalty.[3] If done at the time of a SaaS launch, or a FinTech hit by international news, that allows headroom when traffic soars, but no spending on the purchase of bandwidth for the rest of the month.
The hardware specification is also quite lavish; even the entry-level models come with current multi-core CPUs and SSD storage. Single-core legacy boxes can only be found in a museum rack and should not be considered in a 2025 capacity plan at all.
Energy-Efficient Tier III+ Facilities Cut Opex
TCO consists of capital outlay, and power is its other half. As of mid-2026, energy intensity needs to achieve PUE ≤ 1.2 in any new data center. Existing halls will be required to reach ≤ 1.3 by 2030.[4] Cooling and power-train overhead are being squeezed so tightly that electricity is effectively becoming a pass-through expense, rather than a profit center. This means tenants will enjoy reduced price per kilowatt and stable utility overcharges, despite increasingly dense workloads.
How Does DE-CIX Peering from Frankfurt Cut EU Latency?
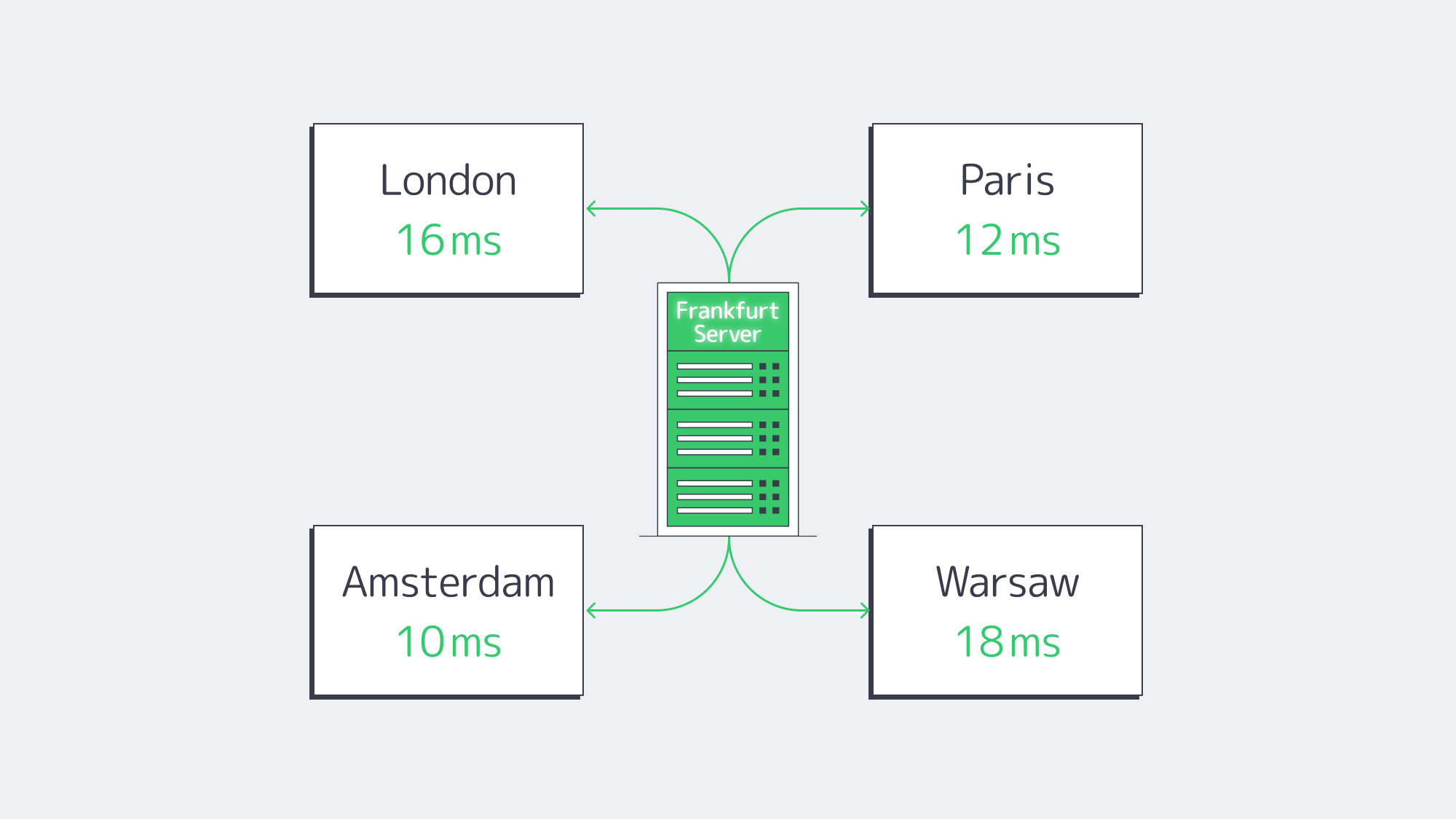
Frankfurt moves packets like no other European city. In November 2024, DE-CIX Frankfurt reached a record high of 18.1 Tbps, holding the highest single-site traffic throughput globally.[5] It supports over 1,100 networks on its exchange, with most of its end-user routes staying on-exchange, eliminating milliseconds of backtracking. Geography takes care of the rest: Frankfurt lies roughly equidistant from London, Paris, Amsterdam, and Warsaw, keeping fiber miles to a minimum.
Typical round-trip times (RTT):
| City | RTT (ms) | Source |
|---|---|---|
| London | 16.5 | wondernetwork.com |
| Paris | 12.0 | wondernetwork.com |
| Amsterdam | 9–11 | DE-CIX Looking-Glass |
Why Do Sub-20 ms Latency Numbers Matter for Users and APIs?
An API in Frankfurt can be faster for a London-based fintech client compared to a London-based API reaching Warsaw. Frankfurt also retains ~85 ms to New York and <140 ms to the U.S. West Coast, so it is also possible to configure transatlantic SaaS residency with no user-noticeable latency.
Which Industries See Revenue Gains from Lower Latency in Germany?
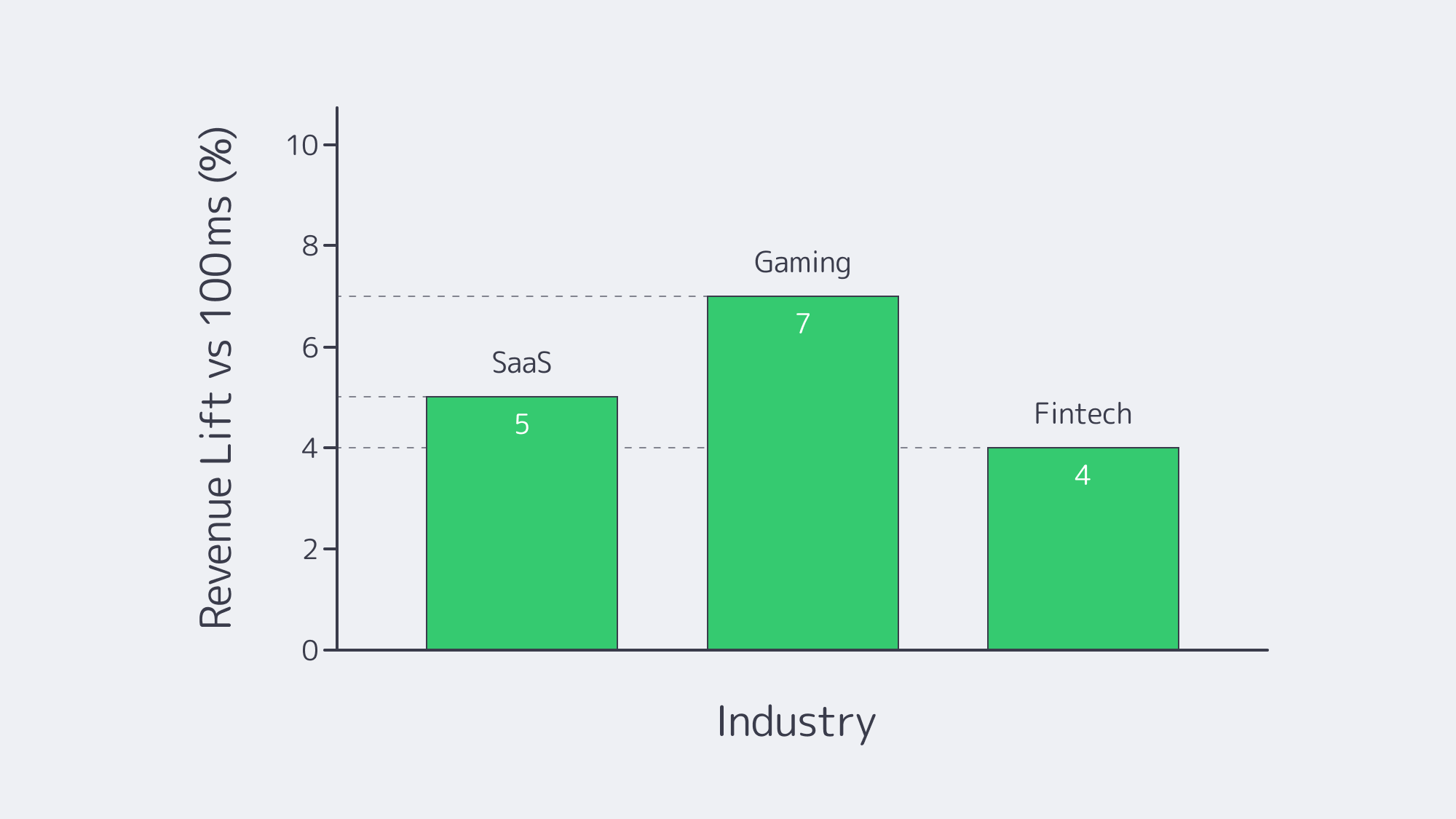
SaaS: Milliseconds Guard MRR
The powerful observation made by Amazon, which found that an additional 100 ms of latency reduces sales by 1 percent, is now estimated to be too low.[6] Today, Akamai can find up to 7 percent cart-conversion loss at the same 100 ms. In a SaaS company with an ARR of 10 million euros, thirty additional milliseconds can destroy hundreds of thousands of euros a year. With an anchor in Frankfurt, even a simple dedicated server in Germany ensures that UI round-trips in Europe-wide are in the teens, and a difference in the UI round-trip time between a Paris user and a Dublin user is essentially equal to the time it takes someone to react.
Fintech & HFT: Milliseconds Mean Millions
Trading desks measure latency in euros per basis point; studies of high-frequency trading demonstrate that a 1 ms delay can cost millions annually.[7] The colocation cages in Frankfurt are metres away from the Eurex and Xetra engines, so a direct fibre jumper (a cross-connect) lends < 50 µs of one-way latency, which is close to the theoretical speed-of-light limit inside the campus. Shorter round-trips between acquirer, issuer, and fraud-scoring engines also reduce card-authorisation times, lowering cart abandonment.
What Sets Melbicom’s Frankfurt Dedicated Servers Apart?
We at Melbicom rely on this German quality, but with the elimination of the acquisition hassle. There are nearly 200 configurations on the Frankfurt floor ready to deploy, including entry-level 4-core servers to GPU-accelerated servers. The stock list is updated hourly, so startups spin up real hardware—no noisy neighbours—in minutes, then scale west to Amsterdam or east to Warsaw on the same backbone. 95th-percentile burst billing comes standard, and ports upsize to 200 Gbps without requiring iperf contortions, with 24/7 support that answers calls in minutes.
Why Germany Is a Low-Latency, Cost-Efficient Choice for Dedicated Servers
Over recent years, architects have believed that they were forced to make a trade-off between low-cost servers in second-tier markets or high performance in hot markets such as London. Frankfurt turned that equation upside down. An oversupplied data-center pipeline and the gravitational effect of DE-CIX have driven price and performance to the same position on the curve, which is not common in infrastructure economics. When you can cover all of the most significant EU population centers in 20 ms or less and continue paying second-tier rates, the choice is easy.
Germany’s dedicated servers should not, then, be seen as a compromise for budget- and user-experience-driven startups, but rather as a starting point. Tier III+ energy-efficient data centers with a limit on power expenses, network expenses, burstable billing constraints, and a network of nearby peers cut latency down to single digits. Irrespective of whether the burden is a latency-sensitive trading cache or a multi-tenant SaaS application, Germany dedicated hosting can deliver without blowing the budget.
Deploy in Germany Today
Launch high-performance dedicated servers in our Tier III Frankfurt facility within minutes—enterprise bandwidth, low latency, zero setup fees.
Get expert support with your services
Blog
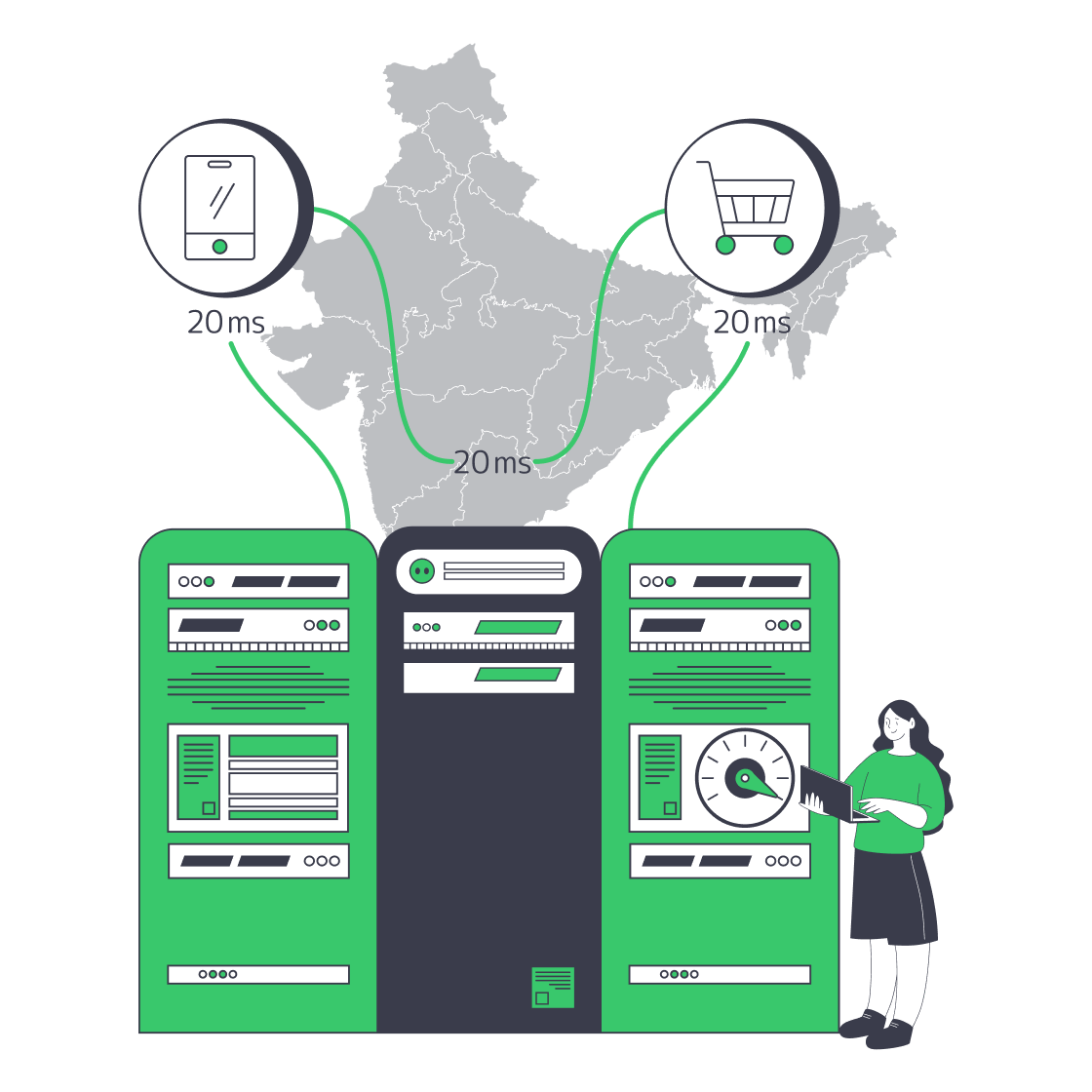
Why Indian Dedicated Servers Slash Cart Abandonment
The Indian online retail market has surged to a gross merchandise value of $60 billion and is currently one of the top three markets by the number of customers worldwide. [1] Indian customers often use smartphones to complete purchases (81 per cent of all buyers do so). They can no longer tolerate slow websites. 60 percent of all shoppers will leave an application that takes more than 10 seconds to load.[2] Each millisecond counts: Amazon lost 1 % revenue with every additional 100 ms of latency [3], and Akamai recorded a 7 % decrease in conversions at the same level.[4]
Choose Melbicom— Dozens of ready-to-go servers — Tier III-certified DC in Mumbai — 55+ PoP CDN across 6 continents |
 |
An Indian dedicated server eliminates ocean distance, meets the new Indian privacy regime, and taps directly into metro areas that are retrofitting 400 GbE fabrics. We outline below the operationalized key dimensions that CTOs are currently calculating: performance, compliance, infrastructure depth, and peak-season resilience, and how Melbicom can assist in converting them into revenue.
Dedicated Server in India: Slashing Last-Mile Latency
When an Indian customer clicks a checkout button and the request is stopped in Europe or North America, the round-trip time often exceeds 150 ms.. Mumbai hosting reduces that to 20-50 ms, clearing the so-called last-mile drag that increases Time-to-First-Byte and, consequently, Largest Contentful Paint (LCP). The payoff is visible:
- Faster LCP & INP. Shorter transport means headers appear sooner, render-blocking scripts start sooner, and the main thread is done clearing sooner. 30–50 % LCP improvements have been documented by many Indian sites when origin servers are moved back to in-country.
- More predictable tails. Single-tenant hardware eliminates the contentious behavior of “noisy neighbors” on shared clouds, and thus its P95 and P99 latencies decrease in tandem with the average.
- Bandwidth headroom. Indian modern dedicated servers are typically shipped with 10G, 40G, or even 200Gbps bandwidth plans that should be sufficient for 4K product video or on-device AI inference streams.
Why dedicated server hosting in India beats distant clouds
The cloud regions outside India hide the latency of CDN edges but the API calls concerning carts, business logic and real-time inventory will always leave the local network. Proximity wins when the work involves the type of request where a request has revenue risk as with a checkout, payments, or personalization. In contrast with shared instances, dedicated servers keep kernel-to-NIC control in your control where its performance is capable of being optimized by the seconds by performance engineers with tuned TCP stacks or QUIC optimizations.
Meeting DPDP Act Compliance with Dedicated Server Hosting in India

The Digital Personal Data Protection Act (DPDP 2023) in India tightened the screws on international transfers: data can leave to a government-whitelisted set of nations, the so-called trusted nations; and contravention may lead to fines up to 250 crore (approximately US 30 million) or 2 % of global turnover, whichever is higher. [5] The easiest legal position an enterprise can take is to store and process within India when addresses, payment tokens, or behavioral profiles are concerned. A local dedicated server does that in a stroke:
- Data stays onshore. There is no Standard Contractual Clauses or risk assessment to all table replication jobs
- Audit-ready visibility. Physical control, in combination with logs within the same jurisdiction, reduces the number of regulator enquiries.
- Consumer trust. Surveys indicate that privacy is a higher priority for most Indian users when selecting a platform compared to price.
By hosting servers in ISO-27001 Indian Tier-III data centres, Melbicom provides needed paperwork to compliance groups without affecting performance.
Where Should You Deploy—Mumbai, Chennai, or Delhi-NCR?
India’s data-centre landscape has leap-frogged legacy constraints. Total installed IT load crossed 1,263 MW in April 2025—a 3.6 × jump since 2020—and is racing toward 4.5 GW by 2030.[6] Capacity is heavily concentrated in three metros [7]:
| City | Share of National Capacity | What It Means for Latency |
| Mumbai | 52 % | First hop for 14 subsea cables; dominates west-coast traffic |
| Chennai | 21 % | Fast east-bound routes to SEA and Singapore |
| Delhi-NCR | 9 % | Northern edge close to government and banking hubs |
Unlike a decade ago, when diesel backups and brownouts scared CIOs, today’s facilities carry dual grid feeds, N+N UPS, and 99.98 % design uptime. Redundant fiber rings and carrier-neutral meet-me rooms allow tenants to multi-home without leaving the building.
Capacity trajectory
| Year | Installed Capacity (MW) |
| 2019 | 350 |
| 2024 | 1 ,030 |
| 2025 | 1 ,263 [7] |
| 2027 (est.) | 1 ,800 [8] |
| 2030 (est.) | 4 ,500 |
Growth is propelled by AI workloads, and hyperscalers alone have pre-committed ≈ 800 MW for new GPU clusters and by e-commerce platforms localizing under DPDP. For CTOs, that means plentiful rack space, competitive pricing, and carrier diversity in every major zone.
400 G Peering Fabrics Power AI-Rich Commerce
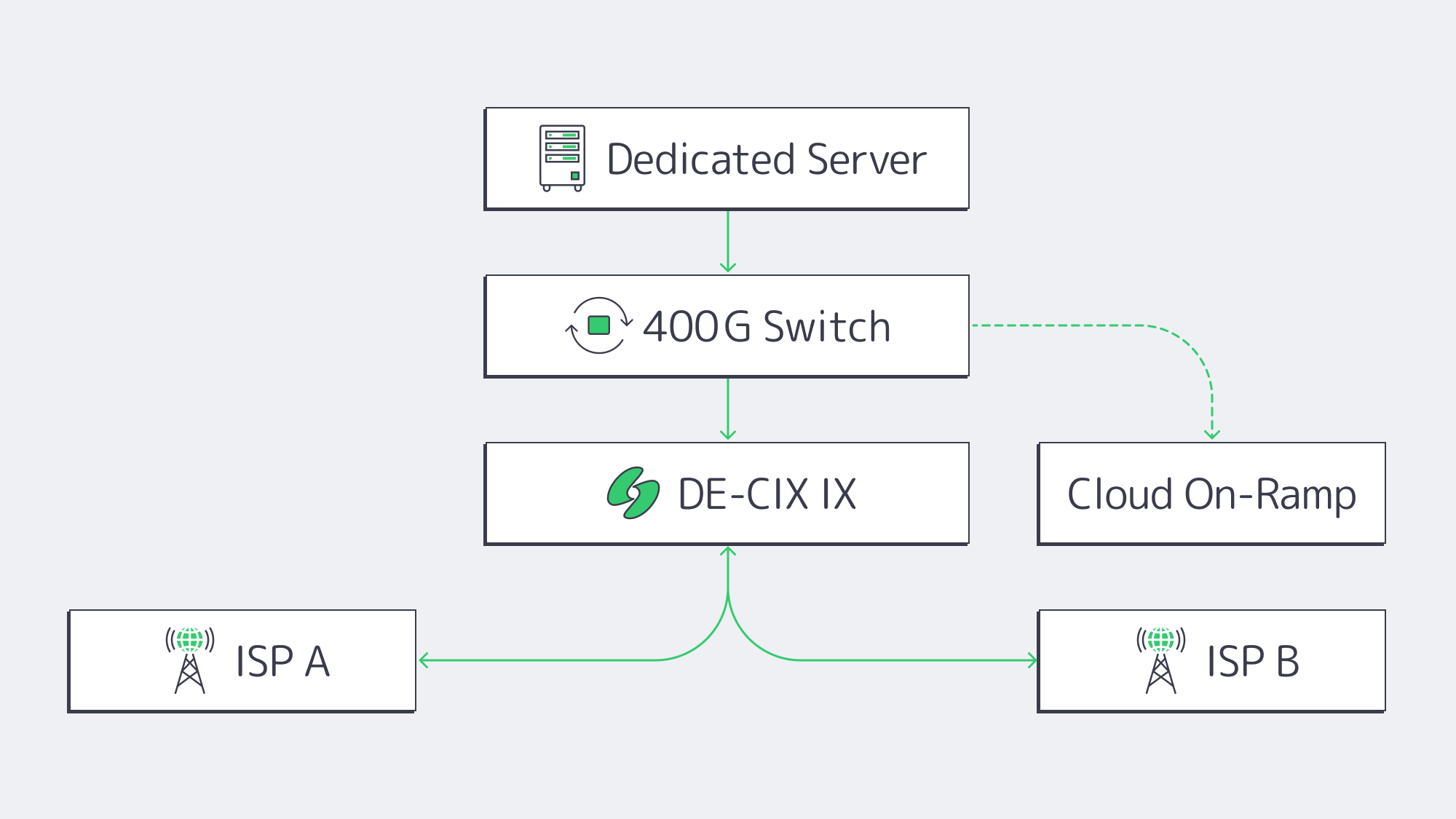
Closeness is irrelevant where the packets stack up at choke points. The leading IXPs in India are rectifying that. In 2023, DE-CIX Mumbai expanded to 400 GbE access ports and achieved a peak of 1.5 Tbps, representing a 32% yearly increase. [9] NIXI is undertaking similar upgrade programs on its nodes across the country. The working result is this:
- Sub-10 ms paths across the metro among servers, ISPs, and CDNs that play a critical role in edge inference, live video or AR try-ons.
- Cloud on-ramps within the same facility, meaning that hybrid environments can burst to AWS or Azure, without heading out to the public internet.
- A cheaper price for transit. Dense peering both cuts the cost curve of bandwidth and enables competitive, low-priced dedicated server hosting in India without compromising throughput.
How to Prepare Dedicated Servers in India for Traffic Spikes
Diwali, Navratri, Big Billion Days— the 60-day festival pipeline is now responsible for 35 % to 40% of the annual retail sales [10] and it regularly drives internal traffic 5-10x higher than normal. The 99.9 % uptime guarantee just does not suffice when such a five-minute hiccup burns the quarter profit to ashes.
Key practices we see winning teams adopt:
- Baseline on dedicated iron, burst elastically. Run mission-critical databases and checkout APIs on one (two or more) Indian dedicated servers to avoid latency and much better price-predictability; spin up ephemeral cloud instances behind a load balancer when banners are promoted.
- Run load simulations early. Four-week-ahead synthetic traffic assists in right-sizing CPU, memory, and port speeds.
- Freeze non-essential maintenance. At Melbicom, we facilitate freeze windows, uplift ticket priorities and have on-call NOC engineers.
- Monitor tail latency, not just averages. Slow frames are also abandoned before a complete outage is experienced.
Dedicated Server Hosting in India without Last-Minute Failures
Cheap capacity is void when ports saturate or CPU cores are starved at peak load. Melbicom offers single-tenant systems at budget plans and still wired and ready for true 1-, 5-, or 10 Gbps (and higher) ports and so much more various bandwidths with no oversubscription. This, along with nurturing 24/7 human support provides measurable festival-season headroom, even for emerging brands.
Low-Latency Dedicated Infrastructure, High-Growth Returns
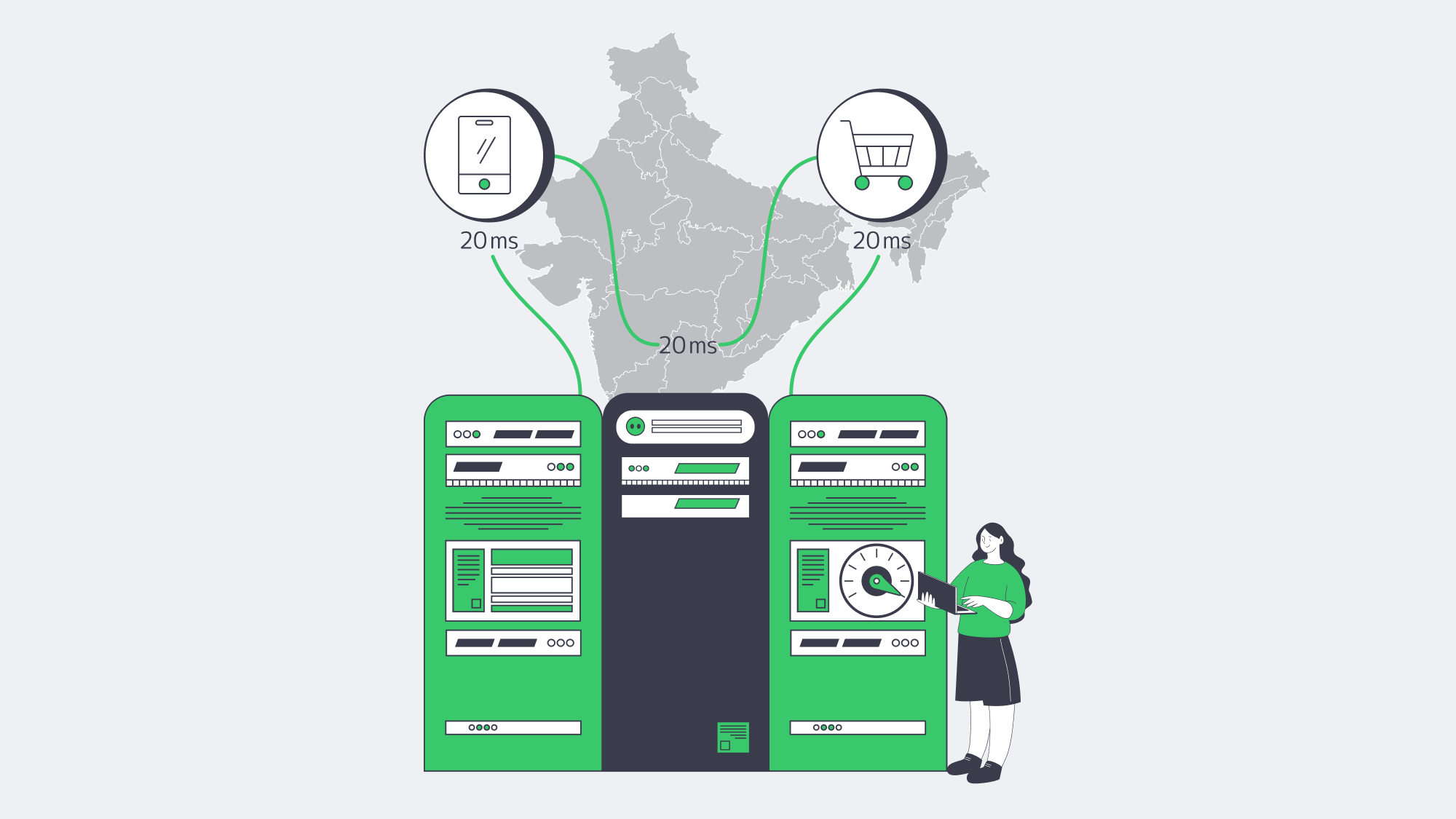
The regional geography, onshore data stewardship, and the metro-edge density have come together to make dedicated servers in India the fastest and most compliant path to scalable growth. CTOs who are familiar with the latency revenue curve are viewing Indian metros as prime deployment areas. The growing presence of Tier-III and even Tier-IV facilities, 400-G IXPs, and growing data-centre capacity adds to a one-year (conservatively) 24 % growth in this capacity, to the point that the ecosystem now matches or exceeds the presence of most Western hubs in income and density, as well as providing cost per delivered gigabyte.
Practically, when the business migrates the latency-sensitive workloads to Mumbai or other Indian cities, it regularly quantifies multi-digit decreases in page-load time, glitch-free Core Web Vitals lists, and stepping-stones to DPDP Act compliance. The infrastructural background is already provided; who takes the first advantage is the winner.
Get your India server now
Deploy a high-performance dedicated server in Mumbai within minutes.
Get expert support with your services
Blog
Find Truly Unlimited Bandwidth Servers in Singapore
Singapore’s strategic perch on Asian fiber routes—combined with a steady decline in wholesale IP-transit rates—has turned unmetered dedicated servers from niche luxury to a mainstream option. There are over 70 carrier-neutral data centers in the area that handle 1.4 GW of installed IT load within the city-state’s 728 km² boundaries. In addition to the infrastructure, regulators have already approved another 300 MW of “green” capacity, so the dense interconnectivity on offer will only grow. This expanding supply and cheaper costs mean that hosts can bundle sizeable, flat-priced ports for mainstream use that previously wouldn’t have been economically viable.[1]
Choose Melbicom— 400+ ready-to-go servers configs — Tier III-certified SG data center — Unmetered bandwidth plans |
 |
These unlimited offers are particularly attractive for buyers dealing in petabytes. Those who stream high-bit-rate videos, for example, are expected to make up roughly 82 percent of all consumer internet traffic this year, according to Cisco.[2] However, “unlimited” might not be as unlimited as it seems on the surface. Many deals still conceal the limits, making it hard to understand what you’re getting. We have compiled a quick guide to help you understand what to audit, measure, and demand when you are in the market for a cheap dedicated Singapore server that needs to work around the clock, flat out.
How to Read an “Unlimited Bandwidth” Offer on Servers
Fair-Use Clauses, TB Figures, and Wiggle Words
First off, be sure to look for fair use triggers in the terms of service. You will likely find something along the lines of “We reserve the right to cap after N PB.” If you deal with large traffic and a limit exists, it should be hundreds of terabytes per Gbps, or removed entirely.
Avoid 95th-Percentile “Bursts”
Some providers disguise the illegitimacy of their unlimited plans through the 95th-percentile billing model. You might find 1 Gbps advertised, but with a guarantee of 250 Mbps sustained; however, should you exceed the percentile threshold, the link becomes throttled or billed at overage rates, which can be costly. These “burst” plans often come from big brands and are being heavily criticized by communities. They essentially drop speeds as soon as the average use climbs.[3] When scanning the documentation, look for words like “burst,” “peak,” “commit,” or specific percentile formulas. If the port is truly unlimited, it will stay unmetered and simply state the speed transparently.
No-Ratio Guarantees and Transparency
If the port is oversubscribed, then “unmetered” is irrelevant. Ideally, you need dedicated capacities with no contention ratios, which means that the full line rate you purchase is solely yours. Marketing claims should be verifiable by looking at real-time graphs with measurable metrics, so that your teams can see the throughput matches. At Melbicom, we are dedicated to providing sole servers with no-ratio guarantees for our clients.
Which Infrastructure Signals Prove a Truly Unlimited Server?
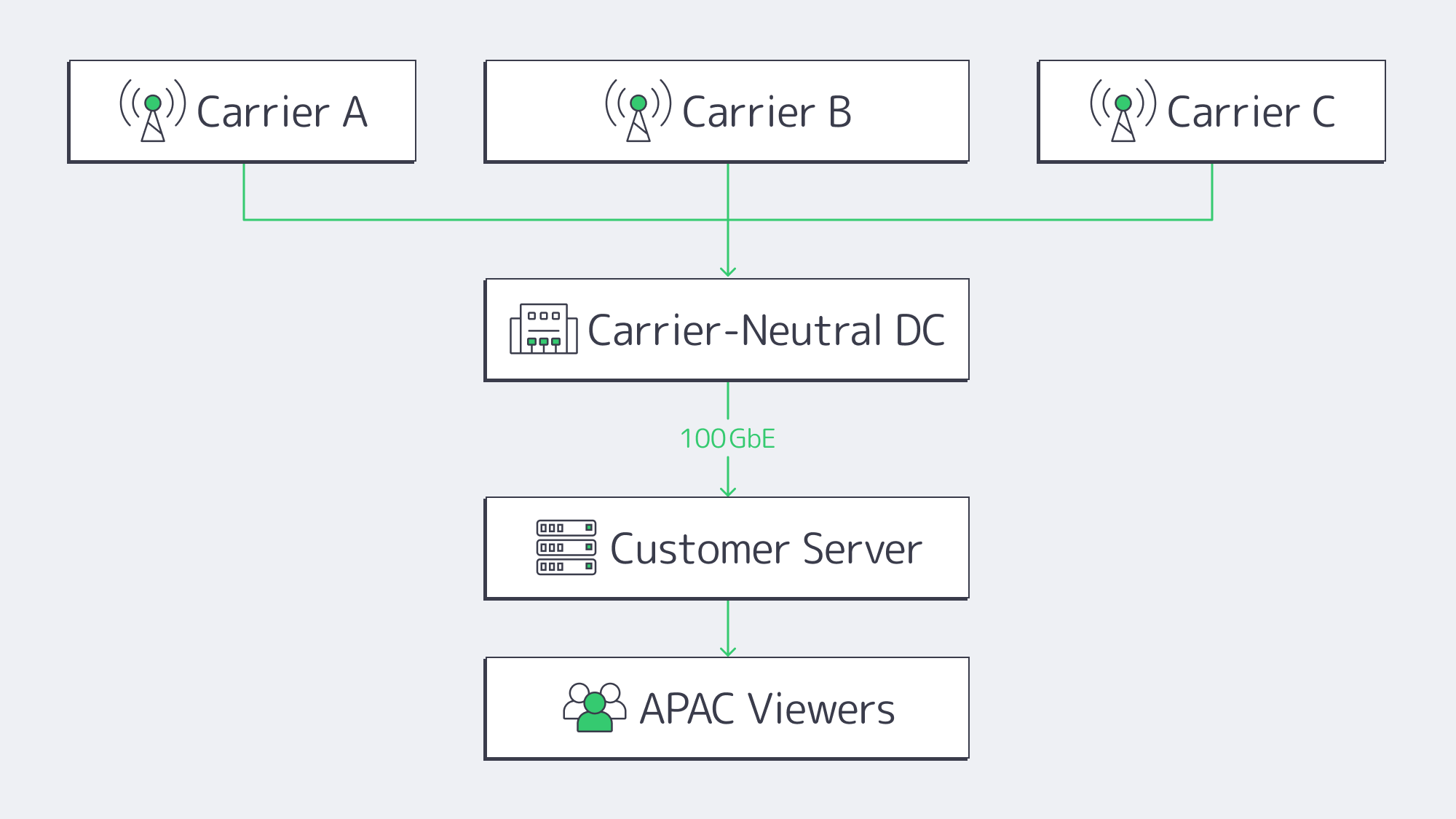
Carrier-Neutral Data Centers
It is wise to prioritize hosts located in carrier-neutral Tier III+ data centers.
- Singapore’s Equinix SG
- Global Switch
- Digital Realty
- SIN1 facilities
Choosing multiple on-net carriers over single-carrier buildings that rely on one upstream prevents the likelihood of silent limits being imposed on heavy users during peaks, ensuring a plentiful upstream capacity and competitive transit rates.
Recent Fiber and Peering Expansion
There are 26 active submarine cable systems in Singapore, and two new Trans-Pacific routes (Bifrost (≃10 Tbps design) and Echo) that land directly on America’s West Coast are scheduled this year to help bypass regional bottlenecks.[5] This will inevitably bring massive headroom for hosts to honor their promises of unmetered server connections.
Port Availability Options
If the vendor has a range of ports available, then it is an infrastructural signal that its back-end capacity can meet unlimited needs. When there are 10 Gbps, 40 Gbps, or 100 Gbps configurations ready to spin up today, you are in good hands. With Melbicom, you can have a Singapore server at 1 to 200 Gbps. Though the upper end may be far more than you need, knowing that you can commit to 1 Gbps with provisions of 100 GbE available gives you the peace of mind that you won’t be oversold gigabit uplinks for your traffic.
How Can You Prove an “Unlimited” Port Is Truly Unlimited?
| Port speed | Max monthly transfer @ 100 % load | Rough equivalence |
|---|---|---|
| 1 Gbps | 330 TB | ≈63 M HD movies |
| 10 Gbps | 3.3 PB | ≈630 M HD movies |
| 100 Gbps | 33 PB | ≈6.3 B HD movies |
Tip: You should be able to move ~330 TB/mo. of any “unmetered 1 Gbps” without incurring any sort of penalty. If there is less stated within the fine print, then it isn’t truly unlimited.
Test what you buy.
- Looking-glass probes – be sure to check multiple continents when you pull vendor sample files. Melbicom’s Singapore facility downloads hover near line rate from well-peered locations.
- Iperf3 marathons – Run Iperf sessions at or near full port speed for at least 6 hours to spot any sudden drops that indicate hidden shaping.
- Peak-hour spot checks – To help detect oversubscription, you can saturate the link during APAC prime time; collective loads shouldn’t decrease with a capable network.
- Packet-loss watch – If a server is truly unlimited, then packet loss should be below 0.5 % during traffic spikes.
The above test will expose any inconsistencies. If discovered, you can invoke the SLA and have the hosts troubleshoot or expand capacity. Reputable hosts that are committed to delivering the throughput that they market should credit your bill.
Why Is “Unlimited Bandwidth” Offer Everywhere Now?
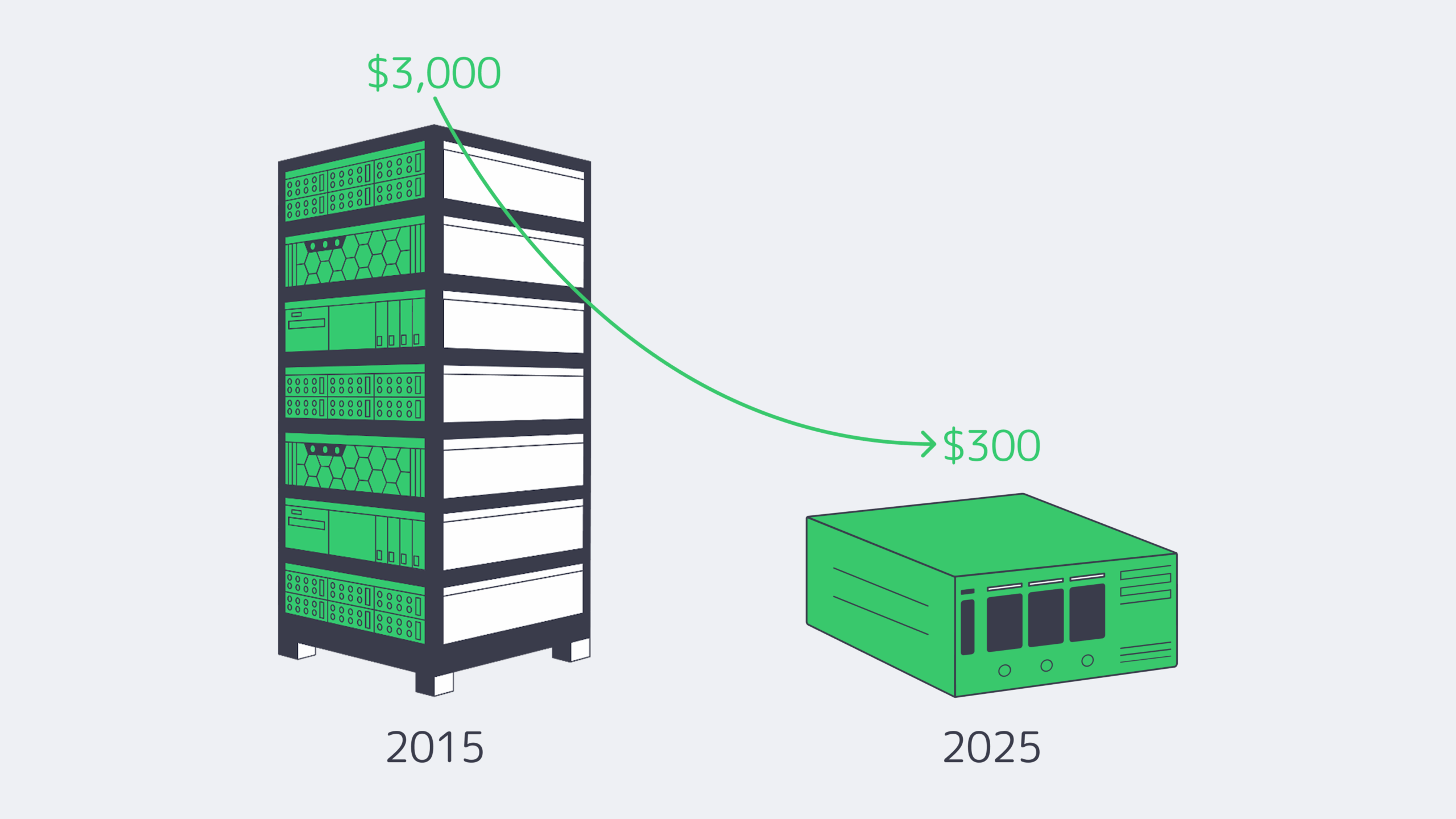
An unmetered 1 Gbps port in Singapore would have set you back roughly US$3,000 per month, minimum, around a decade ago. Bandwidth was once bought wholesale and imposed sky-high 95th-percentile rates. They also rationed it through small TB quotas, making it far less viable for smaller businesses. These days, bulk 100 GbE transit is available for a tenth of the cost, and the prices are continuing to drop as competition and content-provider-funded cables increase in the area.[4]
- Netflix, Meta, and TikTok now have regional caches located within Singapore IXPs, keeping outbound traffic local and avoiding costly subsea hops.
- The Digital Connectivity Blueprint policy that Singapore’s government has put in place links new cables and “green” data-center capacity directly to GDP growth. This speeds up regulatory processes when it comes to network expansion.
- Hosts such as Melbicom have multiple 100 GbE uplinks that span continents. Working at such a scale means adding one more unmetered customer barely affects the commit.
The evolutions mentioned above mean that streaming platforms and other high-traffic clients can get an Asia plan for a dedicated server that rivals European or U.S. pricing without moving away from end-users in Jakarta or Tokyo.
How to Choose an Unlimited-Bandwidth Dedicated Server in Singapore
- Scrutinize the contract. Make sure there are no references to 95th %, burst percentages. If “fair use” is mentioned without revealing the numbers, then steer clear.
- Vet the facility. Prioritize Tier III, carrier-neutral buildings with published lists that can be checked.
- Look for a 100 GbE roadmap. Although you might only need 10 Gbps for now, a roadmap indicates that the provider is a future-proof option.
- Prove and verify marketing spiel and service agreement details. Download test files, run lengthy Iperf tests, and review port graphs.
- Historical context checks. More established hosts could be carrying over outdated caps whereas the raw throughput capabilities provided by modern fiber often means that newer entrants can beat them.
If you can tick the above criteria you have a better chance of having found an authentic, always-on, “unlimited” full-speed dedicated Singapore server.
Why Singapore Is Ready for Truly Unlimited Dedicated Servers
The bandwidth economics in Singapore have evolved: transit is cheaper, budgets are climbing in data centers, and new Terabit-scale cables are on the horizon. It is now possible to obtain the bandwidth needed in Singapore for platforms with demanding, continuous, high-bit-rate traffic affordably and provably without hidden constraints. That is, if you know what to look for!
When just about everybody boasts “unlimited” services and uses jargon to confuse the matter, it can be tougher to separate the smoke from the substance. However, armed with our advice, you should be able to weed out the genuine deals. The upside is that you can quickly separate smoke from substance by checking fair-use language, validating that the data center is carrier-neutral, looking for 100 GbE readiness, and benchmarking sustained throughput against published MSAs.
Order your server
Spin up an unmetered dedicated server in Singapore with guaranteed no-ratio bandwidth.
Get expert support with your services
Blog
Cut EU Latency with Amsterdam Dedicated Servers
Europe’s busiest shopping carts and real-time payment rails live or die on latency. Akamai found that every extra second of page load shaves about 7 % off conversions [1], while Amazon measured a 1 % revenue dip for each additional 100 ms of delay. [2] If your traffic still hops the Atlantic or waits on under-spec hardware, every click costs money. The fastest cure is a dedicated server in Amsterdam equipped with NVMe storage, ECC memory, and multi-core CPUs, sitting a few fibre hops from one of the world’s largest internet exchanges.
Choose Melbicom— 400+ ready-to-go servers configs — Tier IV & III DCs in Amsterdam — 55+ PoP CDN across 6 continents |
 |
This article explains why that combination—plus edge caching, anycast DNS and compute offload near AMS-IX—lets performance-critical platforms treat continental Europe as a “local” audience and leaves HDD-era tuning folklore in the past.
Amsterdam’s Fibre Grid: Short Routes, Big Pipes Network
Amsterdam’s AMS-IX now tops 14 Tbps of peak traffic [3] and connects 1,200 + autonomous systems. [4] That peering density keeps paths short: median round-trip time (RTT) is ≈ 9 ms to London [5], ≈ 8 ms to Frankfurt [6] and only ≈ 30 ms to Madrid [7]. A New-York-to-Frankfurt hop, by contrast, hovers near 90 ms even on premium circuits. Shifting API front ends, auth brokers or risk engines onto a Netherlands server dedicated to your tenancy therefore removes two-thirds of the network delay European customers usually feel.
Melbicom’s presence in Tier III/Tier IV Amsterdam data centers rides diverse dark-fiber rings into AMS-IX, lighting ports that deliver up to 200 Gbps of bandwidth per server. Because that capacity is sold at a flat rate—exactly what unmetered dedicated-hosting customers want—ports can run hot during seasonal peaks without throttling or surprise bills.
First-Hop Wins: Anycast DNS and Edge Caching Acceleration
Latency is more than distance; it is also handshakes. Anycast DNS lets the same resolver IP be announced from dozens of points of presence, so the nearest node answers each query and can trim 20–40 ms of lookup time for global users. Once the name is resolved, edge caching ensures static assets never leave Western Europe.
Because Melbicom racks share the building with its own CDN, a single Amsterdam server can act both as authoritative cache for images, JS bundles and style sheets and as origin for dynamic APIs. GraphQL persisted queries, signed cookies or ESI fragments can be stored on NVMe and regenerated in microseconds, allowing even personalised HTML to ride the low-latency path.
Hardware Built for Micro-Seconds—the Melbicom Way
Melbicom’s Netherlands dedicated server line-up centers on pragmatic, enterprise-grade parts that trade synthetic headline counts for low-latency real-world throughput. There are three ingredients that matter most.
High-Clock Xeon and Ryzen CPUs
Six-core Intel Xeon E-2246G / E-2356G and eight-core Ryzen 7 9700X chips boost to 4.6 – 5 GHz, giving lightning single-thread performance for PHP render paths, TLS handshakes and market-data decoders. Where you need parallelism over sheer clocks, dual-socket Xeon E5-26xx v3 / v4 and Xeon Gold 6132 nodes scale to 40 physical cores (80 threads) that keep OLTP, Kafka and Spark jobs from queueing up.
ECC Memory as Standard
Every Netherlands configuration—whether the entry 32 GB or the 512 GB flagship—ships with ECC DIMMs. Google’s own data center study shows > 8 % of DIMMs experience at least one correctable error per year [8]; catching those flips in-flight means queries never return garbled decimals and JVMs stay up during peak checkout.
Fast Storage Built for Performance
SATA is still the price-per-terabyte king for archives, but performance workloads belong on flash. Melbicom offers three storage tiers:
| Drive type | Seq. throughput | Random 4 K IOPS | Typical configs | Best-fit use-case |
| NVMe PCIe 3.0 | 3 – 3.5 GB/s | 550 K + | 2 × 960 GB NVMe (Xeon E-2276G, Ryzen 7) | hot databases, AI inference |
| SATA SSD | ≈ 550 MB/s | ≈ 100 K | 2 × 480 GB – 1.9 TB (most Xeon E) | catalogue images, logs |
| 10 K RPM HDD | ≈ 200 MB/s | < 200 | 2 × 1 TB + (archive tiers) | cold storage, backups |
* NVMe and SATA figures from Samsung 970 Evo Plus and Intel DC S3520 benchmarks [9];
** HDD baseline from Seagate Exos datasheet.
NVMe latency sits well under 100 µs; that is two orders of magnitude faster than spinning disks and five times quicker than a typical SATA SSD. Write-intensive payment ledgers gain deterministic commit times, and read-heavy product APIs serve cache-misses without stalling the thread pool.
Predictable Bandwidth, no Penalty
Melbicom offers unmetered plans — from 1 to 100 Gbps, and even 200 Gbps — so you never have to micro-optimise image sizes to dodge egress fees. Kernel-bypass TCP stacks and NVMe-oF are allowed full line rate — a guarantee multi-tenant clouds rarely match. In practice, teams pair a high-clock six-core for front-end response with a dual-Xeon storage tier behind it, all inside the same AMS-IX metro loop: sub-10 ms RTT, sub-1 ms disk, and wires that never fill.
Designing for Tomorrow, Not Yesterday
Defrag scripts, short-stroking platters and RAID-stripe gymnastics were brilliant in the 200 IOPS era; today they are noise. Performance hinges on:
- Proximity – keep RTT under 30 ms to avoid cart abandonment.
- Parallelism – 64 + cores erase queueing inside the CPU.
- Persistent I/O – NVMe drives cut disk latency to microseconds.
- Integrity – ECC turns silent corruption into harmless logs.
- Predictable bandwidth – flat-rate pipes remove the temptation to throttle success.
Early-hint headers and HTTP/3 push the gains further, and AMS-IX already lights 400 G ports [11], so protocol evolution faces zero capacity hurdles.
Security and Compliance—Without Slowing Down Performance
The Netherlands pairs a strict GDPR regime with first-class engineering. Tier III/IV power and N + N cooling deliver four-nines uptime; AES-NI on XEON encrypts streams at line rate, so privacy costs no performance. Keeping sensitive rows on EU soil also short-circuits legal latency: auditors sign off faster when data never crosses an ocean.
Turning Milliseconds Into Market Leadership
Latency is not a footnote—it is a P&L line. Parking workloads on dedicated server hosting equipped with NVMe, ECC RAM and multi-thread CPUs puts your stack within arm’s reach of 450 million EU consumers. Anycast DNS and edge caching shave the first round-trips; AMS-IX’s dense peering erases the rest; NVMe and XEON cores finish the job in microseconds. What reaches the shopper is an experience that feels instant—and a checkout flow that never gives doubt time to bloom.
Launch High-Speed Servers Now
Deploy a dedicated server in Amsterdam today and cut page load times for your EU customers.
Get expert support with your services
Blog

Speed and Collaboration in Modern DevOps Hosting
Modern software teams live or die by how quickly and safely they can push code to production. High-performing DevOps organizations now deploy on demand—hundreds of times per week—while laggards still fight monthly release trains.
To close that gap, engineering leaders are refactoring not only code but infrastructure: they are wiring continuous-integration pipelines to dedicated hardware, cloning on-demand test clusters, and orchestrating microservices across hybrid clouds. The mission is simple: erase every delay between “commit” and “customer.”
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Below is a data-driven look at the four tactics that matter most—CI/CD, self-service environments, container orchestration, and integrated collaboration—followed by a reality check on debugging speed in dedicated-versus-serverless sandboxes and a brief case for why single-tenant servers remain the backbone of fast pipelines.
CI/CD: The Release Engine
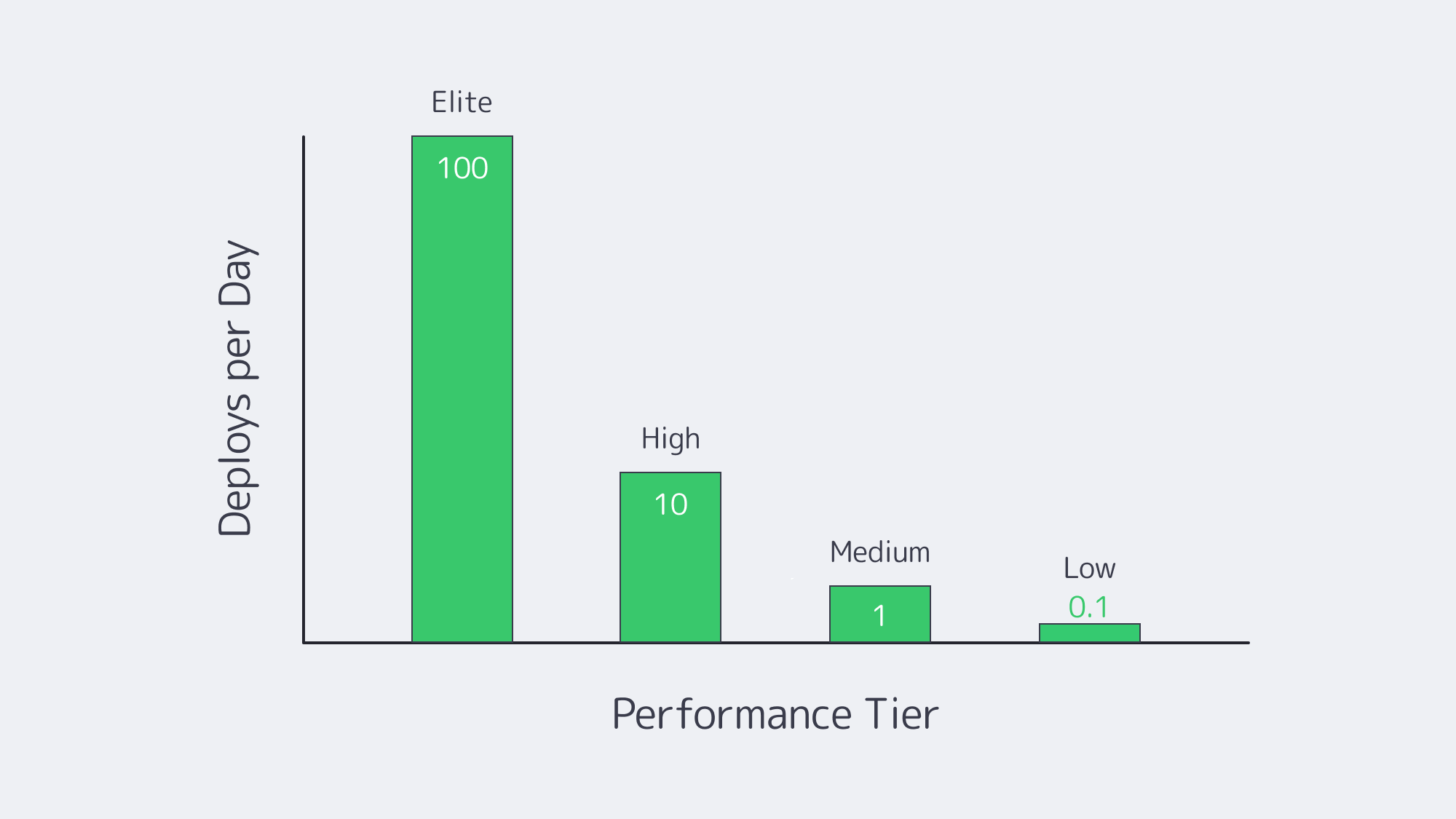
Continuous integration and continuous deployment have become table stakes—83 % of developers now touch CI/CD in their daily work.[1] Yet only elite teams convert that tooling into true speed delivering 973 × more frequent releases with three orders of magnitude faster recovery times than the median.
Key accelerators
| CI/CD Capability | Impact on Code-to-Prod | Typical Tech |
|---|---|---|
| Parallelized test runners | Cuts build times from 20 min → sub-5 min | GitHub Actions, GitLab, Jenkins on auto-scaling runners |
| Declarative pipelines as code | Enables one-click rollback and reproducible builds | YAML-based workflows in main repo |
| Automated canary promotion | Reduces blast radius; unlocks multiple prod pushes per day | Spinnaker, Argo Rollouts |
Many organizations still host runners on shared SaaS tiers that queue for minutes. Moving those agents onto dedicated machines—especially where license-weighted tests or large artifacts are involved—removes noisy-neighbor waits and pushes throughput to line-rate disk and network. Melbicom provisions new dedicated servers in under two hours and sustains up to 200 Gbps per machine, allowing teams to run GPU builds, security scans, and artifact replication without throttling.
Self-Service Environments: Instant Sandboxes
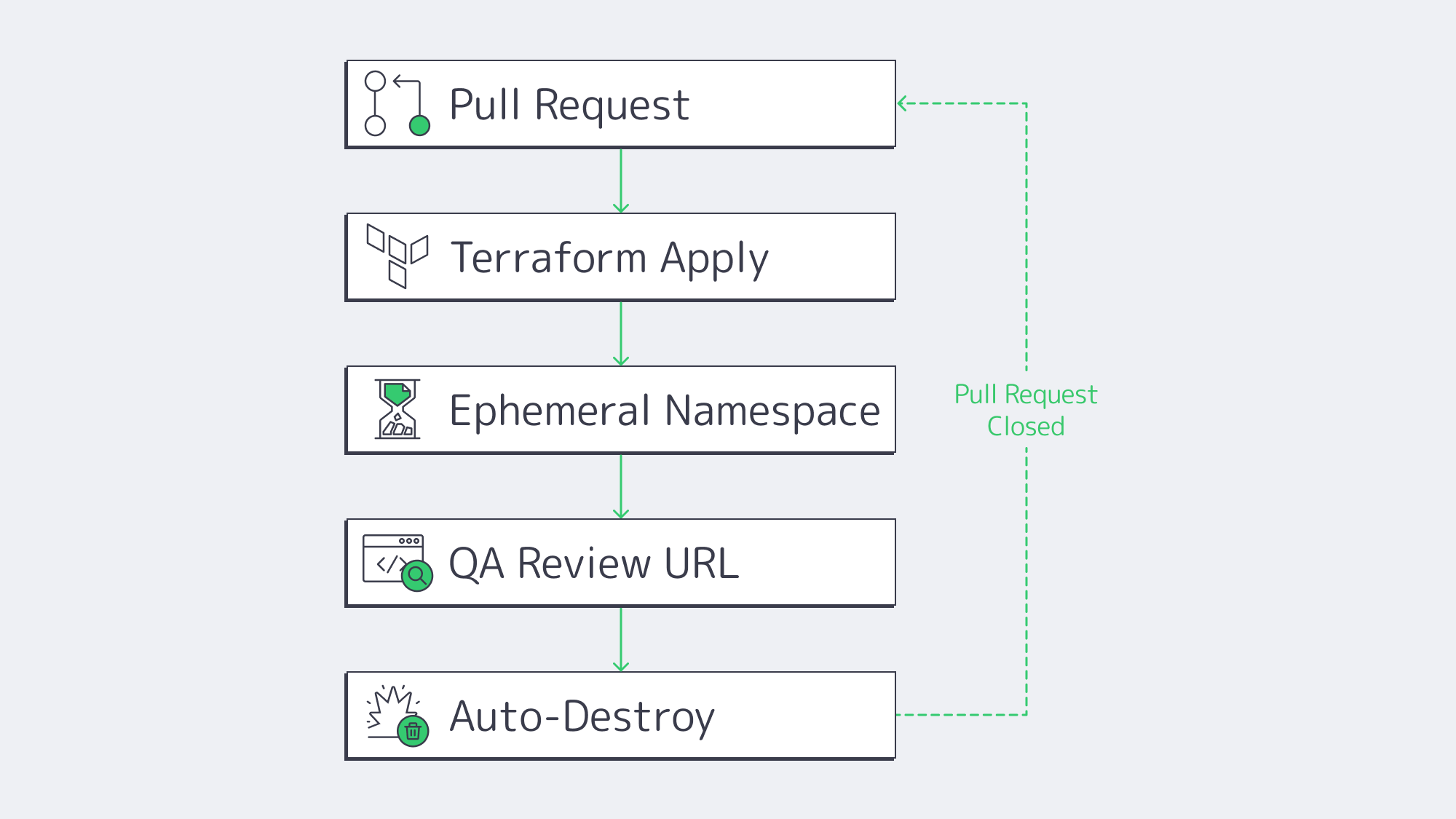
Even the slickest pipeline stalls when engineers wait days for a staging slot. Platform-engineering surveys show 68 % of teams reclaimed at least 30 % developer time after rolling out self-service environment portals. The winning pattern is “ephemeral previews”:
- Developer opens a pull request.
- Pipeline reads a Terraform or Helm template.
- A full stack—API, DB, cache, auth—spins up on a disposable namespace.
- Stakeholders click a unique URL to review.
- Environment auto-destroys on merge or timeout.
Because every preview matches production configs byte-for-byte, integration bugs surface early, and parallel feature branches never collide. Cost overruns are mitigated by built-in TTL policies and scheduled shutdowns. Running these ephemerals on a Kubernetes cluster of dedicated servers keeps cold-start latency near zero while still letting the platform burst into a public cloud node pool when concurrency spikes.
Container Orchestration: Uniform Deployment at Scale
Containers and Kubernetes long ago graduated from buzzword to backbone—84 % of enterprises already evaluate K8s in at least one environment, and two-thirds run it in more than one.[2] For developers, the pay-off is uniformity: the same image, health checks, and rollout rules apply on a laptop, in CI, or across ten data centers.
Why it compresses timelines:
- Environmental parity. “Works on my machine” disappears when the machine is defined as an immutable image.
- Rolling updates and rollbacks. Kubernetes deploys new versions behind readiness probes and auto-reverts on failure, letting teams ship multiple times per day with tiny blast radii.
- Horizontal pod autoscaling. When traffic spikes at 3 a.m., the control plane—not humans—adds replicas, so on-call engineers write code instead of resizing.
Yet orchestration itself can introduce overhead. Surveys find three-quarters of teams wrestle with K8s complexity. One antidote is bare-metal clusters: eliminating the virtualization layer simplifies network paths and improves pod density. Melbicom racks server fleets with single-tenant IPMI access so platform teams can flash the exact kernel, CNI plugin, or NIC driver they need—no waiting on a cloud hypervisor upgrade.
Integrated Collaboration: Tooling Meets DevOps Culture
Speed is half technology, half coordination. High-velocity teams converge on integrated work surfaces:
- Repo-centric discussions. Whether on GitHub or GitLab, code, comments, pipeline status, and ticket links live in one URL.
- ChatOps. Deployments, alerts, and feature flags pipe into Slack or Teams so developers, SREs, and PMs troubleshoot in one thread.
- Shared observability. Engineers reading the same Grafana dashboard as Ops spot regressions before customers do. Post-incident reports feed directly into the backlog.
The DORA study correlates strong documentation and blameless culture with a 30 % jump in delivery performance.[3] Toolchains reinforce that culture: if every infra change flows through a pull request, approval workflows become social, discoverable, and searchable.
Debugging at Speed: Hybrid vs. Serverless
Nothing reveals infrastructure trade-offs faster than a 3 a.m. outage. When time-to-root-cause matters, always-on dedicated environments beat serverless sandboxes in three ways:
| Criteria | Dedicated Servers (or VMs) | Serverless Functions |
|---|---|---|
| Live debugging & SSH | Full access; attach profilers, trace syscalls | Not supported; rely on delayed logs |
| Cold-start latency | Warm; sub-10 ms connection | 100 – 500 ms per wake-up |
| Execution limits | None beyond hardware | Hard caps (e.g., 15 min, 10 GB RAM) |
Serverless excels at elastic front-end API scaling, but its abstraction hides the OS, complicates heap inspection, and enforces strict runtime ceilings. The pragmatic pattern is therefore hybrid:
- Run stateless request handlers as serverless for cost elasticity.
- Mirror critical or stateful components on a dedicated staging cluster for step-through debugging, load replays, and chaos drills.
Developers reproduce flaky edge cases in the persistent cluster, patch fast, then redeploy to both realms with the same container image. This split retains serverless economics and dedicated debuggability.
Hybrid Dedicated Backbone: Why Hardware Still Matters
With public cloud spend surpassing $300 billion, it’s tempting to assume there’s no need for other types of solutions. Yet Gartner forecasts that 90% of enterprises will operate hybrid estates by 2027.[4] Reasons include:
- Predictable performance. No noisy neighbors means latency and throughput figures stay flat—critical when a 100 ms delay can cut e-commerce revenue 1 %.
- Cost-efficient base load. Steady 24 × 7 traffic costs less on fixed-price servers than per-second VM billing.
- Data sovereignty & compliance. Finance, health, and government workloads often must reside in certified single-tenant cages.
- Customization. Teams can install low-level profilers, tune kernel modules, or deploy specialized GPUs without waiting for cloud SKUs.
Melbicom underpins this model with 1,300+ ready configurations across 21 Tier III/IV locations. Teams can anchor their stateful databases in Frankfurt, spin up GPU runners in Amsterdam, burst front-end replicas into US South, and push static assets through a 55-plus-node CDN. Bandwidth scales to a staggering 200 Gbps per box, eliminating throttles during container pulls or artifact replication. Crucially, servers land on-line in two hours, not the multi-week procurement cycles of old.
Hosting That Moves at Developer Speed

Fast, collaborative releases hinge on eliminating every wait state between keyboard and customer. Continuous-integration pipelines slash merge-to-build times; self-service previews wipe out ticket queues; Kubernetes enforces identical deployments; and integrated toolchains keep everyone staring at the same truth. Yet the physical substrate still matters. Dedicated servers—linked through hybrid clouds—sustain predictable performance, deeper debugging, and long-term cost control, while public services add elasticity at the edge. Teams that stitch these layers together ship faster and sleep better.
Deploy Infrastructure in Minutes
Order high-performance dedicated servers across 21 global data centers and get online in under two hours.
Get expert support with your services
Blog
Upgrade to SQL Server 2022 for Peak Performance and Predictable Cost
A production database is one of the fastest aging technologies. However, a survey of thousands of instances under observation reveals that over 30 % of SQL Server implementations are currently running on a release that is already out of extended support, or within 18 months of being out of it. In the meantime, data-hungry applications are demanding millisecond latency and linear scalability—something the older engines were never designed to handle.
The fastest route to both resilience and raw speed is an in-place upgrade to SQL Server 2022. It builds on all the progress in 2019 and adds a second wave of Intelligent Query Processing, latch-free TempDB metadata, and fully inlined scalar UDFs. Before you write your first line of T-SQL, a lot of workloads will perform significantly faster, typically 20-40 % in Microsoft benchmarks, and sometimes by much more than 10 × when TempDB or UDF contention was the underlying problem.
Equally essential, the 2022 release sets the support clock well into the 2030s, so there is no longer the yearly scramble (and cost burden) to keep up with Extended Security Updates. Under a modern license, you have complete certainty about the database’s cost, regardless of how high transaction volumes increase; a type of predictability that is becoming increasingly valuable.
Why Move Now? Support Deadlines and Predictable Costs
SQL Server 2012, 2014, and 2016 either ran out of extended support or are heading to the door in a sprint. Security fixes now require ESUs that begin at 75 % of the original license price in year 1 and increase to 125 % by year 3.[1] Paying such ransom keeps the lights on but can purchase zero performance headroom.
The same is reflected in market data: ConstantCare telemetry data collected by Brent Ozar shows that 2019 already has a 44 % share, with 2022 already surpassing 20 % and being the fastest-growing release.[2] Enterprises are not only jumping on board to keep up with patching, but to get the performance that their peers are already experiencing.
Support Clock at a Glance
| Release | Mainstream End | Extended End |
|---|---|---|
| 2012 | Jul 2017 | Jul 2022 |
| 2014 | Jul 2019 | Jul 2024 |
| 2016 | Jul 2021 | Jul 2026 |
| 2019 | Jan 2025 | Jan 2030 |
| 2022 | Nov 2027 | Nov 2032 |
Table 1. ESUs available at escalating cost through 2025.
The pattern is evident: roughly every three to five years, the floor just falls out under an older release. You are already beyond the safety net regarding 2012 or 2014. People on 2016 only have a year’s worth of fixes left, not even a full QA cycle. Many multi-year migration programs will not complete before SQL Server 2019 loses its mainstream status. Leaping directly to 2022, the runway is extended by a decade, which leaves engineering capacity to complete its features and optimize performance, rather than emergency patch sprints.
How Does SQL Server 2022 Improve Performance on Day One?
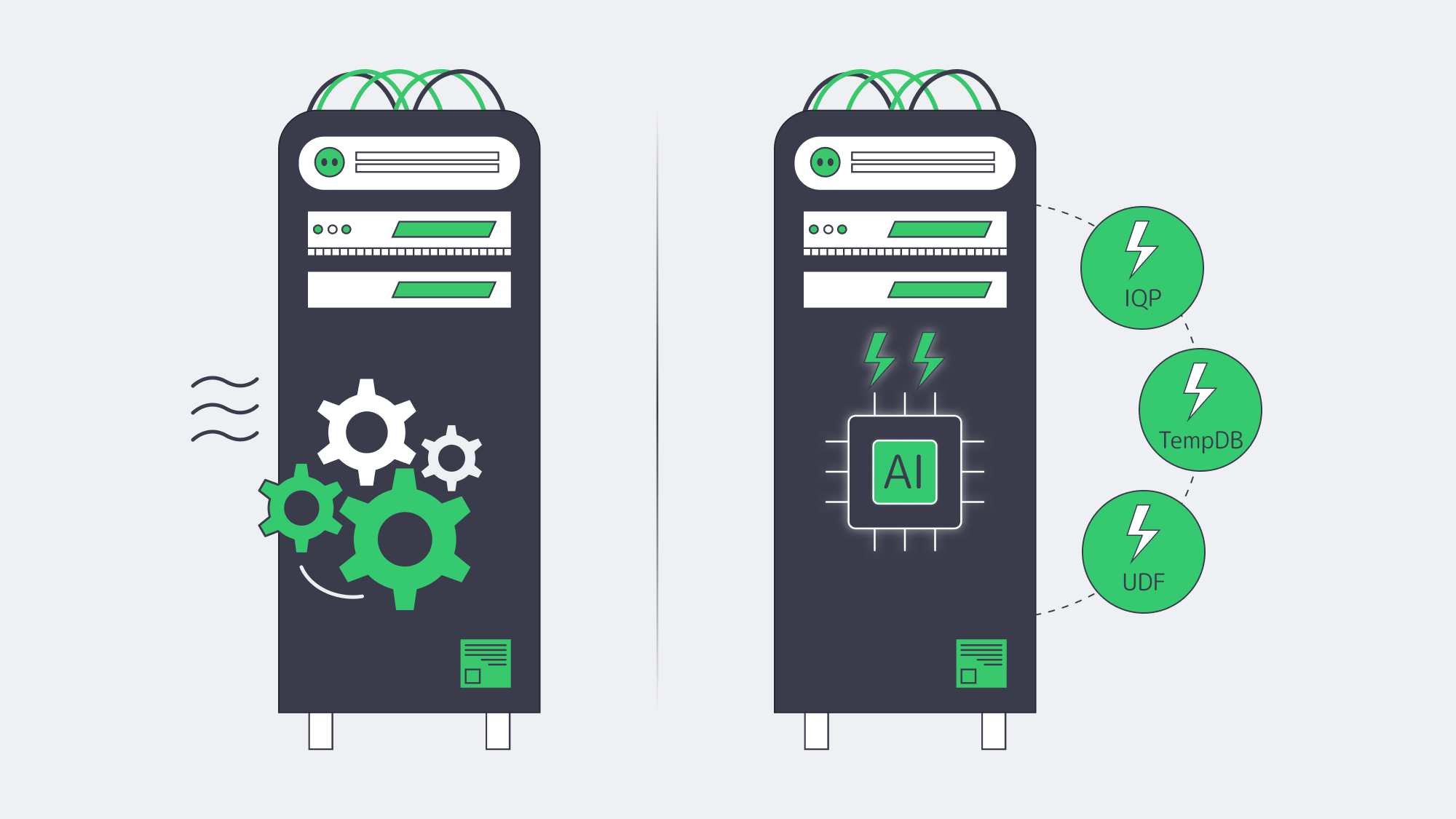
Intelligent Query Processing 2.0
The 2022 release adds Parameter Sensitive Plan optimization and iterative memory grant feedback. The optimizer is allowed to hold multiple plans for the same query and to perfect memory reservations in the long term. Microsoft developers cite 2-5 × speedups on OLTP, including skewed data distributions, without a code change beyond a compatibility level.
Memory-Optimised TempDB Metadata
The TempDB latch waits used to throttle highly concurrent workloads. Microsoft migrated key system tables to latch-free and memory-optimized designs in 2019, and the feature has been enhanced further in 2022. The final bottleneck of the ETL pipelines and nightly index rebuild can be eliminated with one ALTER SERVER CONFIGURATION command.
Accelerated Scalar UDFs
SQL Server 2022 converts scalar UDFs to relational expressions within the primary plan, resulting in orders of magnitude CPU savings where UDFs previously ruled. Add table-variable deferred compilation and rowstore batch mode, and faster backup/restore, and most workloads get measurable gains without code changes.
Putting the Numbers in Context
The in-house TPC E run of SQL Server 2022 on 64 vCPUs achieved 7,800 tpsE, a 19 % increase over the 6,500 tpsE result achieved by SQL Server 2019 on the same hardware. The 95th percentile latency and CPU utilization also decreased by 82 % to 67 %.
Licensing Choices—Core or CAL, Standard or Enterprise
Licensing is what moves TCO, rather than hardware; hence choose wisely.
| Model | When It Makes Sense | 2022 List Price |
|---|---|---|
| Per Core (Std/Ent) | Internet-facing or > 60 named users; predictable cost per vCPU | Std $ 3,945 / 2 cores Ent $ 15,123 / 2 cores |
| Server + CAL (Std) | ≤ 30 users or devices; controlled internal workloads | $ 989 per server + $ 230 per user/device |
| Subscription (Azure Arc) |
Short-term projects, OpEx accounting, auto-upgrades | Std $ 73 / core-mo Ent $ 274 / core-mo |
Table 2. Open No-Level US pricing — check regional programs.
Example: 100 User Internal ERP
- Server + CAL: $989 + (100 × $230 ) ≈ $24 k
- Per-Core Standard: 4 × 2-core packs × $3,945 ≈ $15.8 k
- Per-Core Enterprise: 4 × 2-core packs × $15,123 ≈ $60.5 k
CAL licensing is 50 % more expensive than per core Standard at 100 users.
Standard or Enterprise?
Standard limits the buffer pool to 128 GB and parallelism to 24 cores, but has the entire IQP stack sufficient for the majority of departmental OLTP.
With all physical cores licensed, Enterprise eliminates hardware limits, enables online indexing operations, multi-replica Availability Groups, data compression, and unrestricted VM permissions. Enterprise pays off when you require more than 128 GB of RAM or multi-database failover.
How Do Dedicated Servers Multiply SQL Server 2022 Gains?
No matter how smart the optimizer is, it cannot outrun a slow disk or a clogged network. SQL Server 2022 on dedicated hardware prevents these noisy neighbour effects that are typical of multi-tenant cloud options and takes advantage of the engine memory bandwidth appetite.
Melbicom delivers servers with up to 200 Gbps of guaranteed throughput and NVMe storage arrays optimized to microsecond I/O. With 21 data centers spread throughout Europe, the Americas, and Asia, databases can be located within a few milliseconds of the user base. Over 1,300 server configurations are deployed within two-hour windows; scale-outs no longer wait months to be procured.
Compliance also increases. Financial regulators are increasingly singling out shared hosting as a site of sensitive workloads. Running SQL Server on bare metal makes audits easy: there are only your applications on the box and you are in control of the encryption keys.
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
How to Upgrade to SQL Server 2022: Implementation Checklist
- Take care of licensing ahead of time. Check audit cores and user counts; then make a decision on whether to reuse licenses with SA or purchase new packs.
- Before and After Benchmark. Take before-and-after wait statistics on the current instance, including the upgrade counts.
- Roll out new features over time. Flip compatibility to 160 in QA, monitor Query Store, and repeat in production
- Enable memory-optimized TempDB metadata. Validate latch waits go away.
- Review hardware headroom. Even when DB-level features are no longer sufficient to fill up the CPU, scaling up clocks or core counts is no problem with dedicated gear.
Automated tooling is beneficial. Query Store retains the plans before the upgrade, and you can override to an old plan in case a regression is observed. Distributed Replay or Workload Tools may be used to record production traffic and replay it onto a test clone, revealing surprises well before go-live. Finally, maintain a rollback strategy: once a database connects to 2022, the engine cannot be rolled back, so only perform a compressed copy-only backup before migrating. Storage is cheap, but downtime is not.
Ready to Modernize Your Data Platform?
SQL Server 2022 reduces latency, minimizes CPU usage, and pushes the next support deadline almost a decade into the future, providing finance with a fixed-cost model. The technical work is done by most teams within weeks, followed by years of operational breathing space.
Get Your Dedicated Server Today
Deploy SQL Server 2022 on high-spec hardware with up to 200 Gbps bandwidth in just a few hours.
Get expert support with your services
Blog

Architecting Minutes-Level RTO with Melbicom Servers
The impact of unplanned downtime for modern businesses is significantly higher than ever before. Research pegs last year’s average cost, which was once around $5,600, at $14,056 per minute for midsize and large organizations, which is intolerable. In situations where real-time transactions are required for operation, every second of downtime equates to revenue loss. Furthermore, it can spell contractual penalties and erode the client and customer trust of the brand. The best preventative measure is storing a fully recoverable copy of critical workloads in a secondary data center. The location should be distant enough to survive regional disasters, yet close and fast for a swift takeover if needed.
Melbicom operates via 21 Tier III and IV facilities; each is connected with high-capacity, private backbone links that are capable of bursting up to 200 Gbps per server. With our operation, architects are able to place primary and secondary—or even tertiary—nodes distinctly. There is no need to change vendors or tooling with our setup to achieve a geographically separated backup architecture. That way, a single-point-of-failure trap is evaded and the result is “near-zero downtime.”
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Why Should You Pair—or Triple—Dedicated Backup Server Nodes?
- Node A and Node B are located hundreds of kilometres apart, serving as production and standby, respectively, and replicating data changes continually.
- Node C is located at a third site to provide an air-gapped layer of safety that can also serve as a sandbox for testing and experimentation without affecting production.
Dual operation absorbs traffic and keeps business running. Shared cloud DR can often run into CPU contention and capacity issues, which is never a problem with physical servers. Likewise, power is never sacrificed; should a problem arise at Site A, there is an instantaneous plan B. Should ransomware encrypt Site A volumes, then Site B boots pre-scripted VMs or dedicated server images. Issues are resolved within minutes. When you consider that statistically only 24% of organisations expect to recover in under ten minutes, Melbicom’s minutes-long RTO demonstrates elite performance.
How Does Block-Level Encrypted Replication Cut RPO and Network Load?
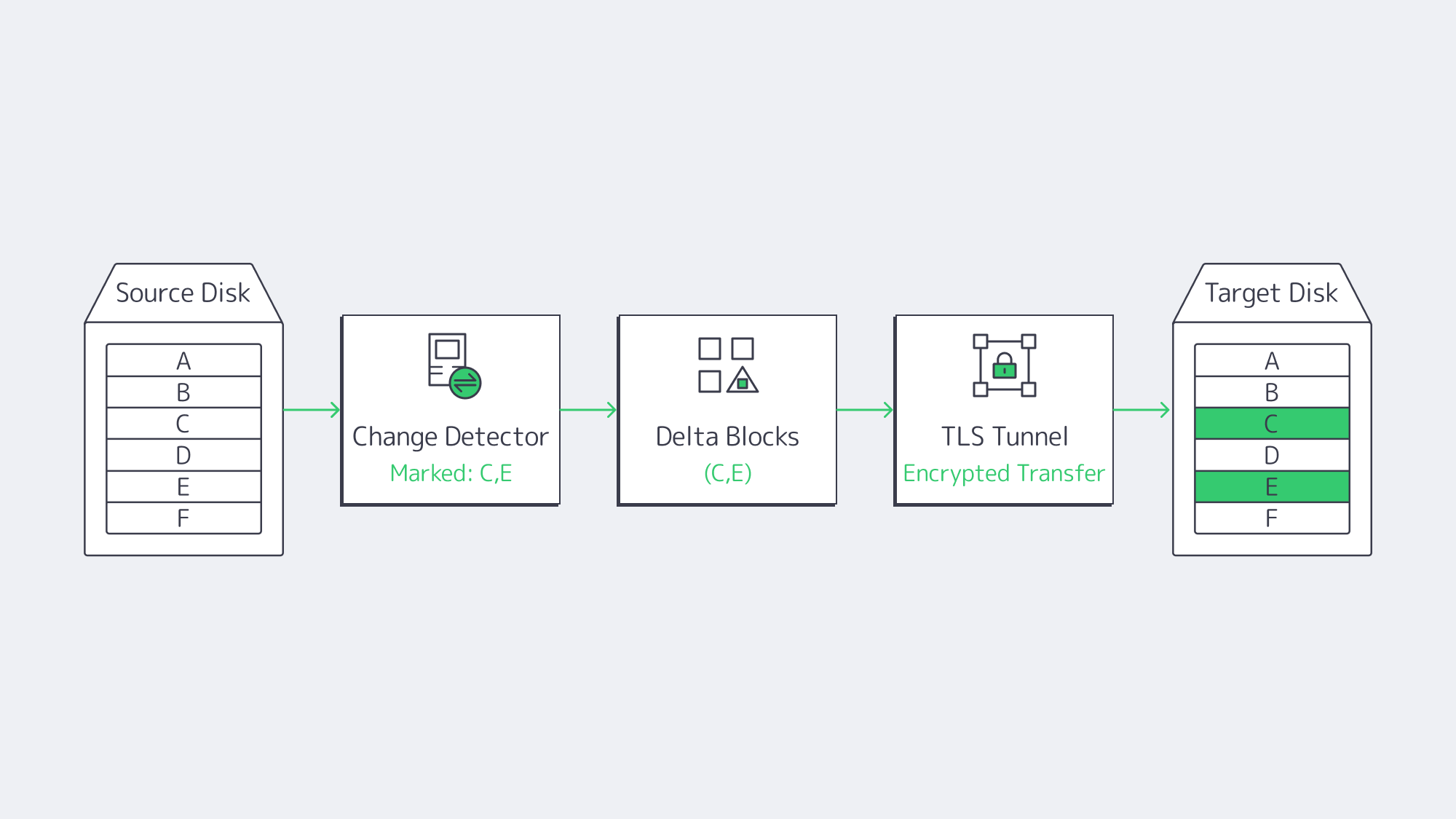
For always-on workloads, copying whole files wastes resources and slows operations. The modern backup solution is to merely capture changed disk blocks in snapshots, streaming solely those deltas to remote storage. In essence, a 10 GB database update that flips 4 MB of pages will only send the 4 MB across the wire, providing the following pay-offs:
- Recovery point objectives (RPOs) of under one minute, irrespective of heavy I/O.
- Bandwidth impact remains minimal during business hours.
- Multiple point-in-time versions are retained without petabytes of duplicate data.
The data is secured by wrapping each replication hop in AES or TLS encryption, keeping it unreadable both in flight and at rest. This satisfies GDPR and HIPAA mandates without the need for any gateway appliances. Melbicom‘s infrastructure encrypts block streams at line rate, and the available capacity is saturated thanks to WAN optimization layers, which we will discuss next.
How Do WAN Acceleration and Burst Bandwidth Speed Initial Seeding?
Separating by distance brings latency, TCP streaming across the Atlantic seldom manages to hit 500 Mbps unassisted. Therefore, bundle WAN accelerators on replication stacks, tuning protocols for inline deduplication and multi-threaded streaming. With WAN acceleration, a 10× data-reduction ratio is achievable even on modest uplinks, allowing 500 Mbit/s of raw change data to move over a 50 Mbit/s pipe in real time, as reported by Veeam.
The most bandwidth-intensive step is the initial transfer, 50 TB over a 1 Gbps link can take almost five days, creating a huge bottleneck, but Melbicom has a workaround. You can opt in for a 100 or even 200 Gbps server bandwidth on the initial replication burst and then switch to a more affordable plan. That way, the full dataset loads at the secondary node in less than an hour. Once the baseline is complete, you can downgrade to 1 Gbps for block-level delta transfers, keeping ongoing costs minimal and production workloads smooth.
Spinning Up Scripted VM & Dedicated Server
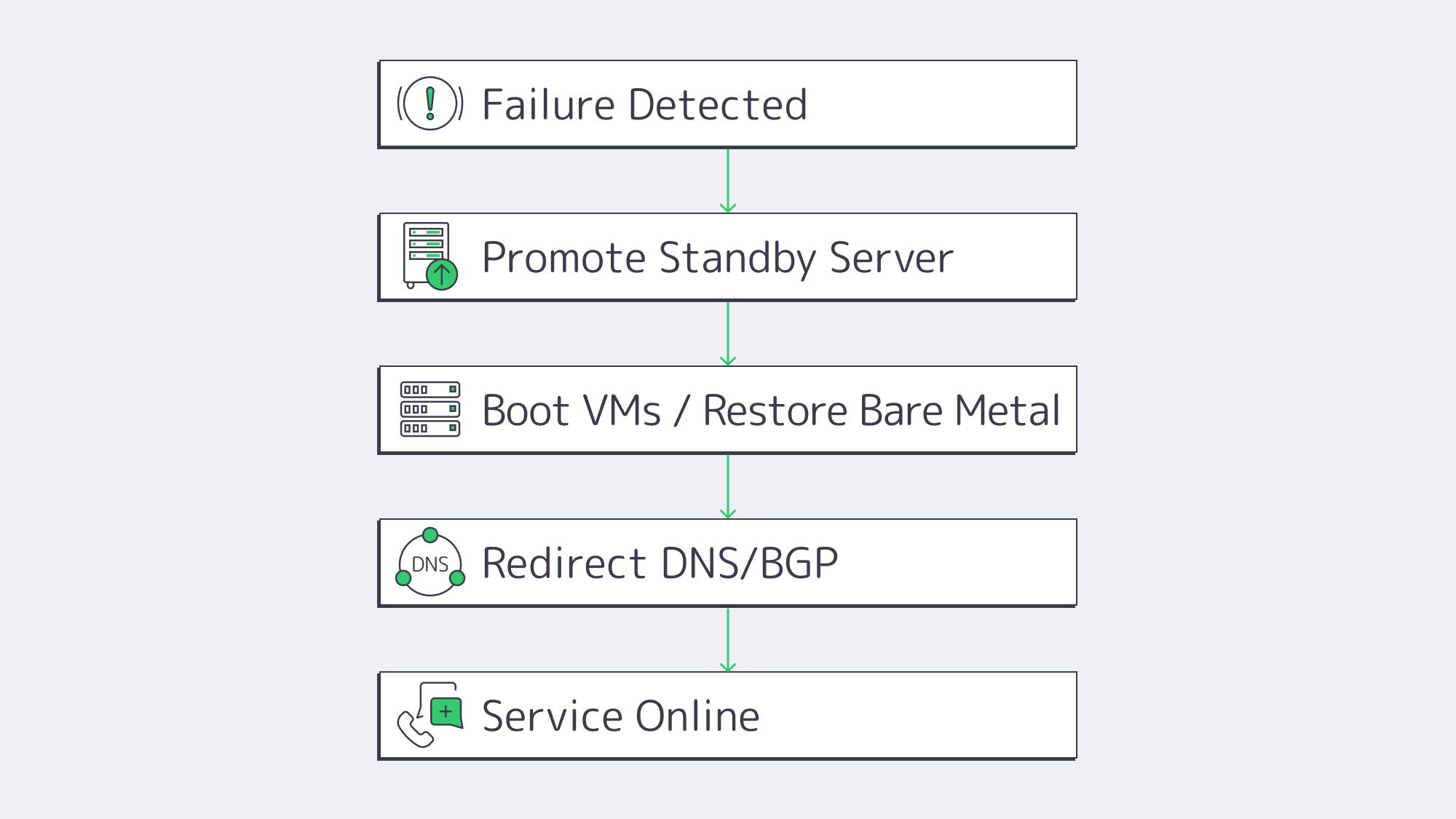
Replicated bits are no use if rebuilding your servers means a ton of downtime. That’s where Instant-Recovery and Dedicated-Server-Restore APIs scripts come into play. The average runbook looks something like this:
- Failure detected; Site A flagged offline.
- Scripts then promote Node B and register the most recent snapshots as primary disks.
- Critical VMs are then booted directly from the replicated images by the hypervisor on Node B through auto-provisioning. The dedicated server workloads PXE-boot into a restore kernel that blasts the image to local NVMe volumes.
- User sessions are swiftly redirected toward Site B via BGP, Anycast, or DNS updates using authentication caches and transactional queues to help identify where they left off and resume activity.
Because the hardware is already live in Melbicom‘s rack, total elapsed time equals boot time plus DNS / BGP convergence—often single-digit minutes. For compliance audits, scripts can run weekly fire-drills that execute the same steps in an isolated VLAN and email a readiness report.
| Backup Strategy | Typical RTO | Ongoing Network Load |
|---|---|---|
| Hot site (active-active) | < 5 min | High |
| Warm standby (replicated dedicated server) | 5 – 60 min | Moderate |
| Cold backup (off-site tape) | 24 – 72 h | Low |
Warm standby—the model enabled by paired Melbicom nodes—delivers a sweet spot between cost and speed, putting minutes-level RTO within reach of most budgets.
Designing for Growth & Threat Evolution
Shockingly, 54 % of organisations still lack a fully documented DR plan, despite 43 % of global cyberattacks now targeting SMBs. For these smaller enterprises, the downtime is unaffordable, highlighting the importance of resilient architecture that can be scaled both horizontally and programmatically:
- Horizontal scale—Melbicom has 1,300+ ready-to-go server configurations that can be provisioned in under two hours. They range from 8-core edge boxes to 96-core, 1 TB RAM monsters, and a further tertiary node can be spun up without procurement cycles in a different region.
- Programmatic control—Backup infrastructure versions alongside workloads as Ansible, Terraform, or native SDKs turn server commissioning, IP-address assignment, and BGP announcements into code.
- Immutable & air-gapped copies—Write-Once-Read-Many (WORM) flags on Object-storage vaults add insurance against ransomware threats.
In the future, anomaly detection will likely be AI-driven, marking suspicious data patterns such as mass encryption writes, automatically snapshotting clean versions to prevent contamination in an out-of-band vault before contamination spreads. Protocols such as NVMe-over-Fabrics will shrink failover performance gaps as they promise to make remote-disk latencies indistinguishable from local NVMe. As these advances come, Melbicom’s network will slot neatly in because it already supports sub-millisecond inter-rack latencies inside key metros with high-bandwidth backbone trunks between.
SMB Accessible
The sophistication of modern backup solutions is often considered to be “enterprise-only,” and so midsize businesses often opt for VMs, but the reality is that 75 % of SMBs, if hit by ransomware, would be forced to cease operations due to the devastation of downtime. The price of a midrange server lease at Melbicom is worth every penny, providing a single dedicated backup server in a secondary site through block-level replication of data secured with high-level encryption brings peace of mind. There is no throttling, and recoveries run locally at LAN speed, and automation is especially beneficial to smaller operations with limited IT teams.
Geography, Speed, and Automation: Make the Most of Every Minute
Current downtime trend statistics all signal that outages are costlier, attackers are quicker, and customer tolerance is lower. Thankfully, by geographically separating production and standby services like we do here at Melbicom, you have the cornerstone of a defensive blueprint. Securing operations requires block-level, encrypted replication for near-perfect sync. Data streams then need compression and WAN acceleration, seeding the first copy offline, and scripting the spin-ups. That way, you have a failover that is integrated into daily workflows. Executing this defense blueprint slashes an enterprise’s RTO to minutes and ensures that even the most catastrophic outage is merely a blip.
Get Your Backup-Ready Server
Deploy a dedicated server in any of 21 Tier III/IV locations and achieve minutes-level disaster recovery.
Get expert support with your services
Blog
Beyond Free: Building Bullet-Proof Server Backups
Savvy IT leads love the price tag on “free,” but experience shows that what you don’t pay in license fees you often pay in risk. The 2024 IBM “Cost of a Data Breach” study pegs the average incident at $4.88 million—the highest on record.[1] Meanwhile, ITIC places downtime for an SMB at $417–$16,700 per server‐minute.[2] With those stakes, backups must be bullet-proof. This piece dissects whether free server backup solutions—especially those pointed at a dedicated off-site server—can clear that bar, or whether paid suites plus purpose-built infrastructure are the safer long-term play.
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Are Free Server Backup Solutions Secure and Reliable Enough?
Why “Free” Still Sells
Free and open-source backup tools (rsync, Restic, Bacula Community, Windows Server Backup, etc.) thrive because they slash capex and avoid vendor lock-in. Bacula alone counts 2.5 million downloads, a testament to community traction. For a single Linux box or a dev sandbox, these options shine: encryption, basic scheduling, and S3-compatible targets are a CLI away. But scale, compliance and breach recovery expose sharp edges.
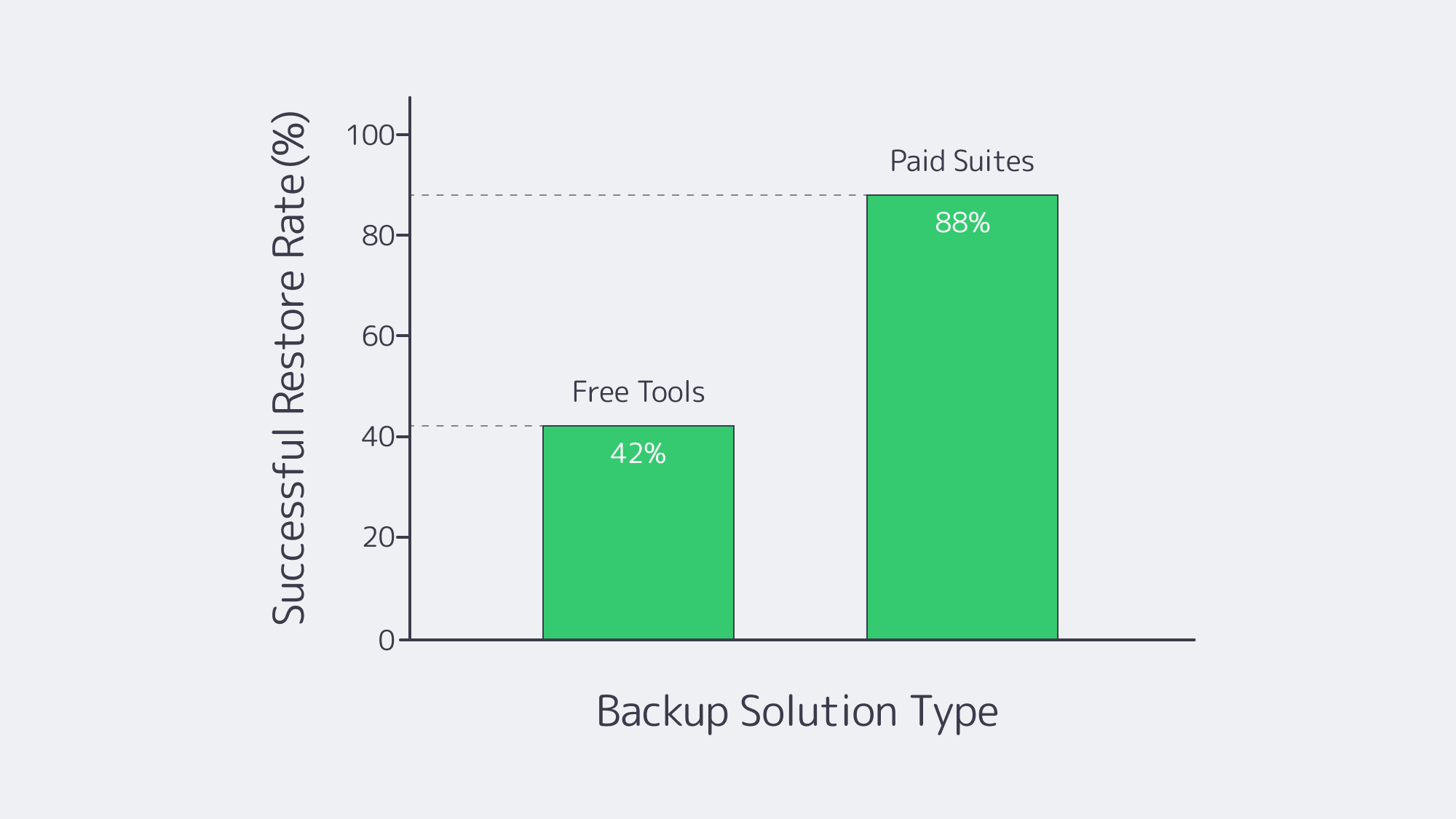
Reliability: A Coin-Toss You Can’t Afford
Industry surveys show 58-60 % of backups fail during recovery—often due to silent corruption or jobs that never ran.[3] Worse, 31 % of ransomware victims cannot restore from their backups, pushing many to pay the ransom anyway.[4] Free tools rarely verify images, hash files, or alert admins when last night’s job died. A mis-typed cron path or a full disk can lurk undetected for months. Paid suites automate verification, catalog integrity, and “sure-restore” drills—capabilities that cost time to script and even more to test if you stay free.
Automation & Oversight: Scripts vs. Policy Engines
Backups now span on-prem VMs, SaaS platforms, and edge devices. Free solutions rely on disparate cron tasks or Task Scheduler entries; no dashboard unifies health across 20 servers. When auditors ask for a month of success logs, you grep manually—if the logs still exist. Enterprise platforms ship policy-driven scheduling, SLA dashboards and API hooks that shut down noise. Downtime in a for-profit shop is measured in cash; paying for orchestration often costs less than the engineer hours spent nursing DIY scripts.
Storage Ceilings and Transfer Windows
Free offerings hide cliffs: Windows Server Backup tops out at 2 TB per job, only keeps a single copy, and offers no deduplication. Object-storage-friendly tools avoid the cap but can choke when incremental chains stretch to hundreds of snapshots. Paid suites bring block-level forever-incremental engines and WAN acceleration that hit nightly windows even at multi-terabyte scale.
Ransomware makes scale a security issue too. 94 % of attacks seek to corrupt backups, and a Trend Micro spin on 2024 data puts that number at 96 %.[5] Those odds demand at least one immutable or air-gapped copy—features rarely turnkey in gratis software.
Compliance & Audit Scenarios
GDPR, HIPAA, and PCI now ask not only, “Do you have a backup?” but also, “Can you prove it’s encrypted, tested, and geographically compliant?” Free tools leave encryption, MFA, and retention-policy scripting to the admin. Paid suites ship pre-built compliance templates and immutable logs—an auditor’s best friend when the clipboard comes out. When a Midwest medical practice faced an OCR audit last year, its home-grown rsync plan offered no chain of custody, and remediation fees ran into six figures. Real-world stories like that underscore that proof is part of the backup product.
The Hidden Invoice: Support and Opportunity Cost
Open-source forums are invaluable but not an MSA. During a restore crisis, waiting for a GitHub reply is perilous. Research by DevOps Institute pegs 250 staff-hours per year just to maintain backup scripts; at median engineer wages, that’s ~$16K—often more than a mid-tier commercial license. Factor in the reputational hit when customers learn their data vanished, and “free” becomes the priciest line item you never budgeted.
Why Do Dedicated Backup Servers Improve Security, Speed & Compliance?
| Feature | Free Tool + Random Storage | Paid Suite on Dedicated Server |
|---|---|---|
| End-to-end verification | Manual testing | Automatic, policy-based |
| Immutable copies | DIY scripting | One-click S3/Object lock |
| Restore speed | Best-effort | Instant VM/file-level |
| SLA & 24/7 help | None/community | Vendor + provider |
Isolation and Throughput
Pointing backups to a dedicated backup server in a Tier III/IV data center removes local disasters from the equation and caps attack surface. We at Melbicom deliver up to 200 Gbps per server, so multi-terabyte images move in one night, not one week. Free tools can leverage that pipe; the hardware and redundant uplinks eliminate the throttling that kills backup windows on cheap public VMs.
Geographic Reach and Compliance Flex
Melbicom operates 21 data-center locations across Europe, North America and beyond—giving customers sovereignty choices and low-latency DR access. You choose Amsterdam for GDPR or Los Angeles for U.S. records; the snapshots stay lawful without extra hoops.
Affordable Elastic Retention via S3
Our S3-compatible Object Storage scales from 1 TB to 500 TB per tenant, with free ingress, erasure coding and NVMe acceleration. Any modern backup suite can target that bucket for immutable, off-site copies. The blend of dedicated server cache + S3 deep-archive gives SMBs an enterprise-grade 3-2-1 posture without AWS sticker shock.
Support That Shows Up
We provide 24 / 7 hardware and network support; if a drive in your backup server fails at 3 a.m., replacements start rolling within hours. That safety net converts an open-source tool from a weekend hobby into a production-ready shield.
Free vs. Paid Backup Solutions: Making the Numbers Work
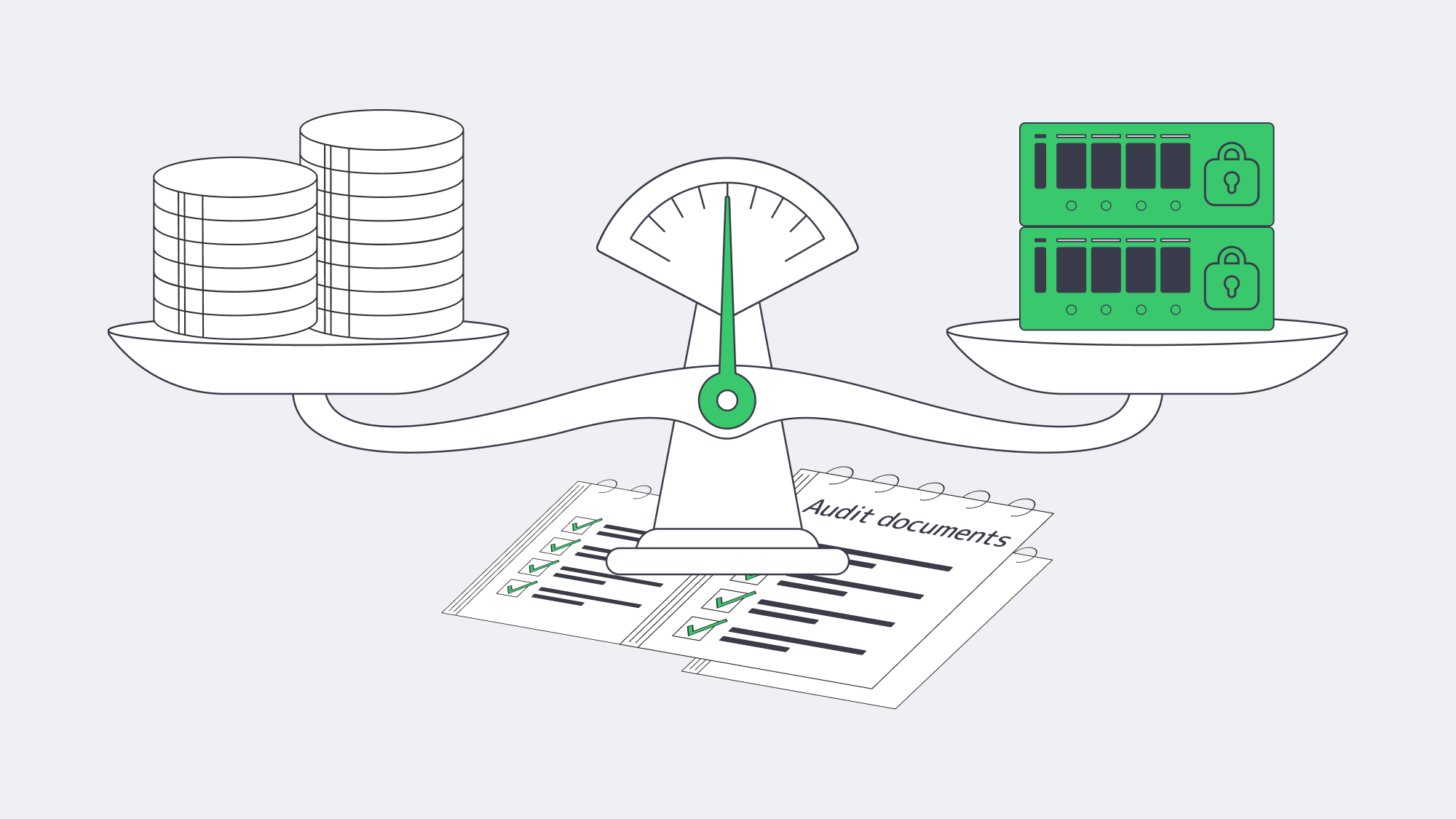
The financial calculus is straightforward: tally the probability × impact of data-loss events against the recurring costs of software and hosting. For many SMBs, a hybrid path hits the sweet spot:
- Keep a trusted open-source agent for everyday file-level backups.
- Add a paid suite or plugin only for complex workloads (databases, SaaS, Kubernetes).
- Anchor everything on a dedicated off-site server with object-storage spill-over for immutable retention.
How to Fortify Backups Beyond Just “Good Enough”
Free server backup solutions remain invaluable in the toolbox—but they rarely constitute the entire toolkit once ransomware, audits and multi-terabyte growth enter the frame. Reliability gaps, manual oversight, storage ceilings and absent SLAs expose businesses to outsized risk. Coupling a robust backup application—open or commercial—with a high-bandwidth, dedicated server closes those gaps and puts recovery time on your side.
Deploy a Dedicated Backup Server
Skip hardware delays—spin up a high-bandwidth backup node in minutes and keep your data immune from local failures.
Get expert support with your services
Blog
Hosting SaaS Applications: Key Factors for Multi‐Tenant Environments
Cloud adoption may feel ubiquitous, yet the economics and physics of running Software-as-a-Service (SaaS) are far from solved. Analysts put total cloud revenues at $912 billion in 2025 and still rising toward the trillion-dollar mark.[1] At the same time, performance sensitivity keeps tightening: Amazon found that every 100 ms of extra latency reduced sales by roughly 1 % [2], while Akamai research shows a seven-percent drop in conversions for each additional second of load time. Hosting strategy therefore becomes a core product decision, not a back-office concern.
Public clouds and container Platform-as-a-Service (PaaS) offerings were ideal for prototypes, but their usage-metered nature introduces budget shocks. Dedicated server clusters—especially when deployed across Melbicom’s Tier III and Tier IV facilities—offer a different trajectory: deterministic performance, full control over data residency and a flat, predictable cost curve. The sections that follow explain how to architect secure, high-performance multi-tenant SaaS systems on Melbicom hardware and why the approach outperforms generic container PaaS at scale.
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Multi-Tenant Reality Check — Single-Tenant Pitfalls in One Paragraph
Multi-tenant design lets one running codebase serve thousands of customers, maximising resource utilisation and simplifying upgrades. Classic single-tenant hosting, by contrast, duplicates the full stack per client, inflates operating costs and turns every release into a coordination nightmare. Except for niche compliance deals, single-tenancy is today a margin-killer. The engineering goal is therefore to make a multi-tenant system behave like dedicated infrastructure for each tenant—without paying single-tenant prices.
How Do Dedicated Server Clusters Create Elastic Resource Pools?
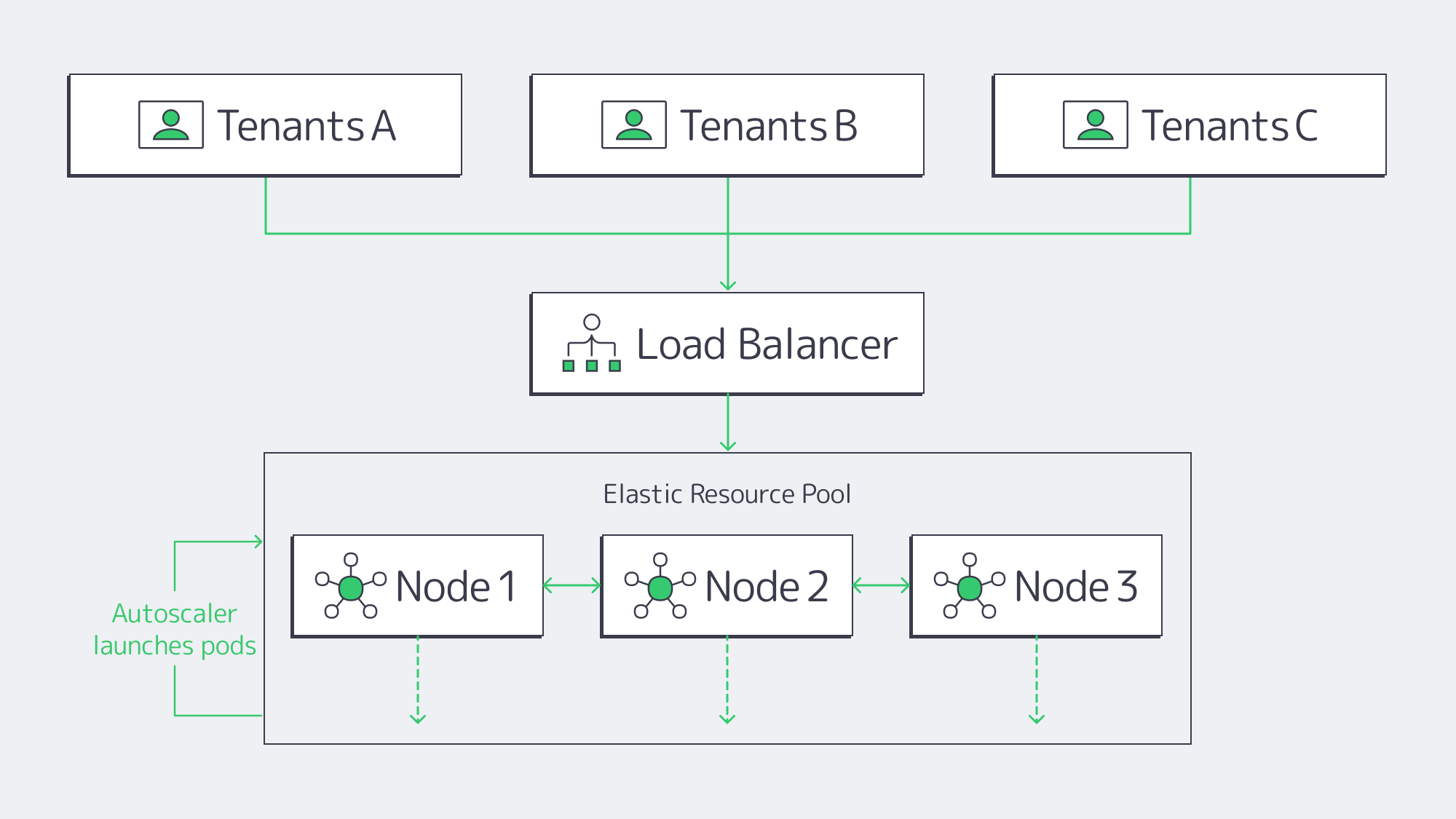
Every Melbicom dedicated server is a physical machine—its CPU, RAM and NVMe drives belong solely to you. Wire multiple machines into a Kubernetes or Nomad cluster and the fixed nodes become an elastic pool:
- Horizontal pod autoscaling launches or removes containers based on per-service metrics.
- cgroup quotas and namespaces cap per-tenant CPU, memory and I/O, preventing starvation.
- Cluster load-balancing keeps hot shards near hot data.
Because no hypervisor interposes, workloads reach the metal directly. Benchmarks from The New Stack showed a bare-metal Kubernetes cluster delivering roughly 2× the CPU throughput of identical workloads on virtual machines and dramatically lower tail latency.[3] Academic studies report virtualisation overheads between 5 % and 30 % depending on workload and hypervisor.[4] Practically, a spike in Tenant A’s analytics job will not degrade Tenant B’s dashboard.
Melbicom augments the design with per-server network capacity up to 200 Gbps and redundant uplinks, eliminating the NIC contention and tail spikes common in shared-cloud environments.
How Do Per-Region Controls Meet Data-Sovereignty Rules?
Regulators now legislate location: GDPR, Schrems II and similar frameworks demand strict data residency. Real compliance is easier when you own the rack. Melbicom operates 21 data centres worldwide—Tier IV Amsterdam for EU data and Tier III sites in Frankfurt, Madrid, Los Angeles, Mumbai, Singapore and more. SaaS teams deploy separate clusters per jurisdiction:
- EU tenants run exclusively on EU nodes with EU-managed encryption keys.
- U.S. tenants run on U.S. nodes with U.S. keys.
- Geo-fenced firewalls and asynchronous replication keep disaster-recovery targets low without breaching residency rules.
Because the hardware is yours, audits rely on direct evidence, not a provider’s white paper.
Zero-Downtime Rolling Upgrades
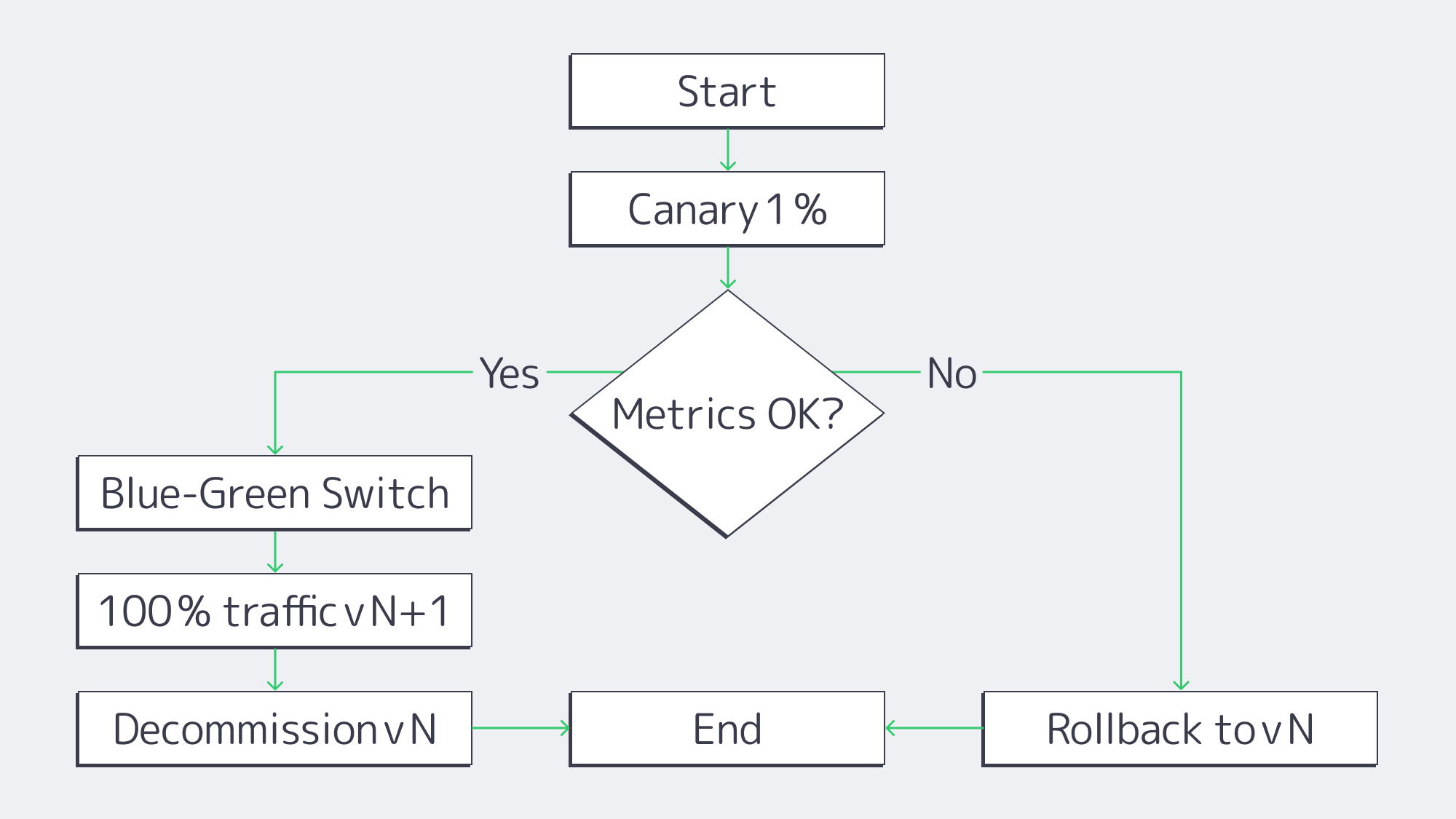
Continuous delivery is table stakes. On a Melbicom cluster the pipeline is simple:
- Canary – Route 1 % of traffic to version N + 1 and watch p95 latency.
- Blue-green – Spin up version N + 1 alongside N; flip the load-balancer VIP on success.
- Instant rollback – A single Kubernetes command reverts in seconds.
Full control of probes, disruption budgets and pod sequencing yields regular releases without maintenance windows.
How Does Physical Isolation Remove Hypervisor Cross-Talk Risks?
Logical controls (separate schemas, row-level security, JWT scopes) are stronger when paired with physical exclusivity:
- No co-located strangers. Hypervisor-escape exploits affecting multi-tenant clouds are irrelevant here—no one else’s VM runs next door.
- Hardware root of trust. Self-encrypting drives and TPM 2.0 modules bind OS images to hardware; supply-chain attestation verifies firmware at boot.
- Physical and network security. Tier III/IV data centers use biometrics and man-traps, while in-rack firewalls keep tenant VLANs isolated.
Predictable Performance Versus Container-Based PaaS Pricing
Container-PaaS billing is advertised as pay-as-you-go—vCPU-seconds, GiB-seconds and per-request fees—but the meter keeps ticking when traffic is steady. 37signals reports ≈ US $ 1 million in annual run-rate savings—and a projected US $ 10 million over five years—after repatriating Basecamp and HEY from AWS to owned racks.[5] Meanwhile, a 2024 Gartner pulse survey found that 69 % of IT leaders overshot their cloud budgets.[6]
Flat-rate dedicated clusters flip the model: you pay a predictable monthly fee per server and run it hot.
| Production-Month Cost at 100 Million Requests | Container PaaS | Melbicom Cluster |
| Compute + memory | US $ 32 (10 × GCP Cloud Run Example 1: $3.20 for 10 M req) (cloud.google.com) | US $ 1 320 (3 × € 407 ≈ US $ 440 “2× E5-2660 v4, 128 GB, 1 Gbps” servers) |
| Storage (5 TB NVMe) | US $ 400 (5 000 GB × $0.08/GB-mo gp3) (aws.amazon.com) | Included |
| Egress (50 TB) | US $ 4 300 10 TB × $0.09 + 40 TB × $0.085 (cloudflare.com, cloudzero.com) | Included |
| Total | US $ 4 732 | US $ 1 320 |
Table. Public list prices for Google Cloud Run request-based billing vs. three 24-core / 128 GB servers on a 1 Gbps unmetered plan.
Performance mirrors the cost picture: recent benchmarks show bare-metal nodes deliver sub-100 ms p99 latency versus 120–150 ms on hypervisor-backed VMs—a 20-50 % tail-latency cut.[7]
How to Achieve Global Low-Latency Delivery for SaaS
Physics still matters—roughly 10 ms RTT per 1 000 km—so locality is essential. Melbicom’s backbone links 21 regions and feeds a 55-plus-PoP CDN that caches static assets at the edge. Dynamic traffic lands on the nearest active cluster via BGP Anycast, holding user-perceived latency under 30 ms in most OECD cities and mid-20s for outliers. The same topology shortens database replication and accelerates TLS handshakes—critical for real-time dashboards and collaborative editing.
How Do Dedicated Clusters Improve Long-Term Economics & Flexibility?
Early-stage teams need elasticity; grown-up teams need margin. Flat-rate dedicated hosting flattens the spend curve: once hardware amortises—servers often run 5–7 years—every new tenant improves unit economics. Capacity planning is painless: Melbicom stocks 1,300+ ready-to-go configurations and can deploy extra nodes in hours. Seasonal burst? Lease for a quarter. Permanent growth? Commit for a year and capture volume discounts. GPU cards or AI accelerators slot directly into existing chassis instead of requiring a new cloud SKU.
Open-source orchestration keeps you free of platform lock-in: if strategy shifts, migrate hardware or multi-home with other providers without rewriting core code.
Dedicated Server Clusters—a Future-Proof Backbone for SaaS
SaaS providers must juggle customer isolation, regulatory scrutiny, aggressive performance targets and rising cloud costs. A cluster of dedicated bare-metal nodes reconciles those demands: hypervisor-free speed keeps every tenant fast, strict per-tenant policies and regional placement satisfy regulators, and full-stack control enables rolling releases without downtime. Crucially, the spend curve flattens as utilisation climbs, turning infrastructure from a volatile liability into a strategic asset.
Hardware is faster, APIs are friendlier, and global bare-metal capacity is now an API call away—making this the moment to shift SaaS workloads from opaque PaaS meters to predictable dedicated clusters.
Order Your Dedicated Cluster
Launch high-performance SaaS on Melbicom’s flat-rate servers today.