Blog

Architecting Minutes-Level RTO with Melbicom Servers
The impact of unplanned downtime for modern businesses is significantly higher than ever before. Research pegs last year’s average cost, which was once around $5,600, at $14,056 per minute for midsize and large organizations, which is intolerable. In situations where real-time transactions are required for operation, every second of downtime equates to revenue loss. Furthermore, it can spell contractual penalties and erode the client and customer trust of the brand. The best preventative measure is storing a fully recoverable copy of critical workloads in a secondary data center. The location should be distant enough to survive regional disasters, yet close and fast for a swift takeover if needed.
Melbicom operates via 21 Tier III and IV facilities; each is connected with high-capacity, private backbone links that are capable of bursting up to 200 Gbps per server. With our operation, architects are able to place primary and secondary—or even tertiary—nodes distinctly. There is no need to change vendors or tooling with our setup to achieve a geographically separated backup architecture. That way, a single-point-of-failure trap is evaded and the result is “near-zero downtime.”
Choose Melbicom— 1,300+ ready-to-go servers — 21 global Tier IV & III data centers — 55+ PoP CDN across 6 continents |
 |
Why Should You Pair—or Triple—Dedicated Backup Server Nodes?
- Node A and Node B are located hundreds of kilometres apart, serving as production and standby, respectively, and replicating data changes continually.
- Node C is located at a third site to provide an air-gapped layer of safety that can also serve as a sandbox for testing and experimentation without affecting production.
Dual operation absorbs traffic and keeps business running. Shared cloud DR can often run into CPU contention and capacity issues, which is never a problem with physical servers. Likewise, power is never sacrificed; should a problem arise at Site A, there is an instantaneous plan B. Should ransomware encrypt Site A volumes, then Site B boots pre-scripted VMs or dedicated server images. Issues are resolved within minutes. When you consider that statistically only 24% of organisations expect to recover in under ten minutes, Melbicom’s minutes-long RTO demonstrates elite performance.
How Does Block-Level Encrypted Replication Cut RPO and Network Load?
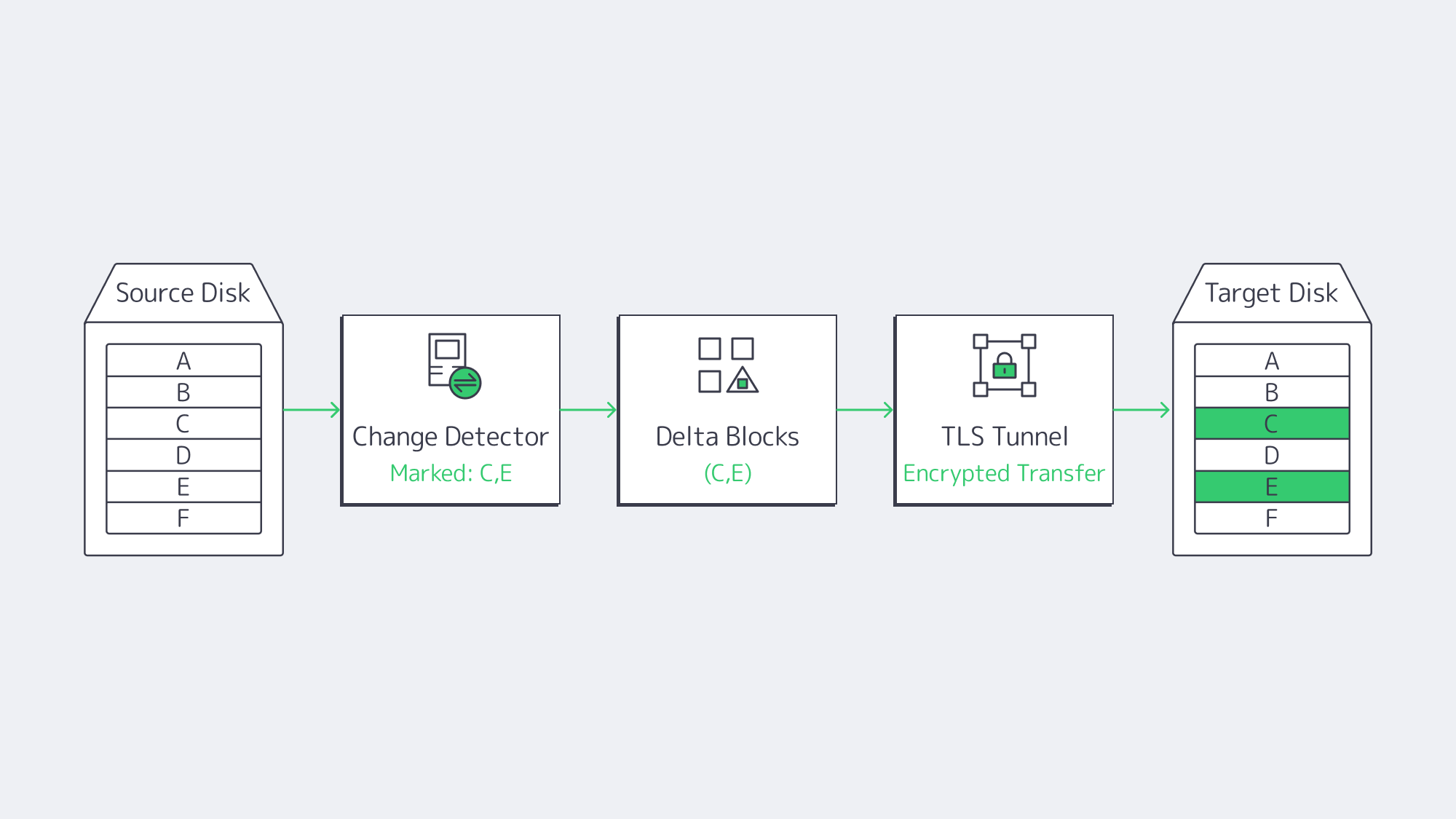
For always-on workloads, copying whole files wastes resources and slows operations. The modern backup solution is to merely capture changed disk blocks in snapshots, streaming solely those deltas to remote storage. In essence, a 10 GB database update that flips 4 MB of pages will only send the 4 MB across the wire, providing the following pay-offs:
- Recovery point objectives (RPOs) of under one minute, irrespective of heavy I/O.
- Bandwidth impact remains minimal during business hours.
- Multiple point-in-time versions are retained without petabytes of duplicate data.
The data is secured by wrapping each replication hop in AES or TLS encryption, keeping it unreadable both in flight and at rest. This satisfies GDPR and HIPAA mandates without the need for any gateway appliances. Melbicom‘s infrastructure encrypts block streams at line rate, and the available capacity is saturated thanks to WAN optimization layers, which we will discuss next.
How Do WAN Acceleration and Burst Bandwidth Speed Initial Seeding?
Separating by distance brings latency, TCP streaming across the Atlantic seldom manages to hit 500 Mbps unassisted. Therefore, bundle WAN accelerators on replication stacks, tuning protocols for inline deduplication and multi-threaded streaming. With WAN acceleration, a 10× data-reduction ratio is achievable even on modest uplinks, allowing 500 Mbit/s of raw change data to move over a 50 Mbit/s pipe in real time, as reported by Veeam.
The most bandwidth-intensive step is the initial transfer, 50 TB over a 1 Gbps link can take almost five days, creating a huge bottleneck, but Melbicom has a workaround. You can opt in for a 100 or even 200 Gbps server bandwidth on the initial replication burst and then switch to a more affordable plan. That way, the full dataset loads at the secondary node in less than an hour. Once the baseline is complete, you can downgrade to 1 Gbps for block-level delta transfers, keeping ongoing costs minimal and production workloads smooth.
Spinning Up Scripted VM & Dedicated Server
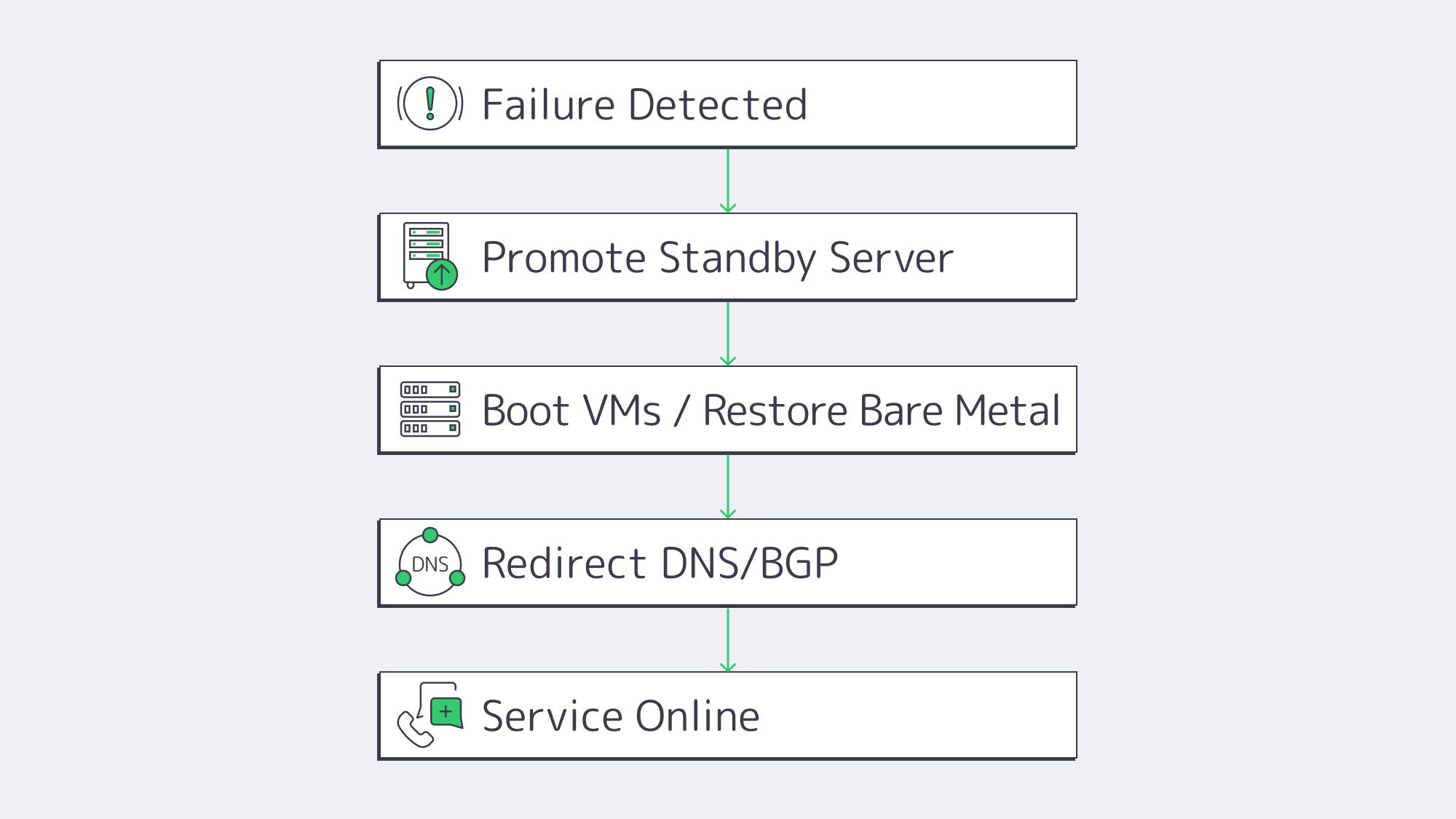
Replicated bits are no use if rebuilding your servers means a ton of downtime. That’s where Instant-Recovery and Dedicated-Server-Restore APIs scripts come into play. The average runbook looks something like this:
- Failure detected; Site A flagged offline.
- Scripts then promote Node B and register the most recent snapshots as primary disks.
- Critical VMs are then booted directly from the replicated images by the hypervisor on Node B through auto-provisioning. The dedicated server workloads PXE-boot into a restore kernel that blasts the image to local NVMe volumes.
- User sessions are swiftly redirected toward Site B via BGP, Anycast, or DNS updates using authentication caches and transactional queues to help identify where they left off and resume activity.
Because the hardware is already live in Melbicom‘s rack, total elapsed time equals boot time plus DNS / BGP convergence—often single-digit minutes. For compliance audits, scripts can run weekly fire-drills that execute the same steps in an isolated VLAN and email a readiness report.
| Backup Strategy | Typical RTO | Ongoing Network Load |
|---|---|---|
| Hot site (active-active) | < 5 min | High |
| Warm standby (replicated dedicated server) | 5 – 60 min | Moderate |
| Cold backup (off-site tape) | 24 – 72 h | Low |
Warm standby—the model enabled by paired Melbicom nodes—delivers a sweet spot between cost and speed, putting minutes-level RTO within reach of most budgets.
Designing for Growth & Threat Evolution
Shockingly, 54 % of organisations still lack a fully documented DR plan, despite 43 % of global cyberattacks now targeting SMBs. For these smaller enterprises, the downtime is unaffordable, highlighting the importance of resilient architecture that can be scaled both horizontally and programmatically:
- Horizontal scale—Melbicom has 1,300+ ready-to-go server configurations that can be provisioned in under two hours. They range from 8-core edge boxes to 96-core, 1 TB RAM monsters, and a further tertiary node can be spun up without procurement cycles in a different region.
- Programmatic control—Backup infrastructure versions alongside workloads as Ansible, Terraform, or native SDKs turn server commissioning, IP-address assignment, and BGP announcements into code.
- Immutable & air-gapped copies—Write-Once-Read-Many (WORM) flags on Object-storage vaults add insurance against ransomware threats.
In the future, anomaly detection will likely be AI-driven, marking suspicious data patterns such as mass encryption writes, automatically snapshotting clean versions to prevent contamination in an out-of-band vault before contamination spreads. Protocols such as NVMe-over-Fabrics will shrink failover performance gaps as they promise to make remote-disk latencies indistinguishable from local NVMe. As these advances come, Melbicom’s network will slot neatly in because it already supports sub-millisecond inter-rack latencies inside key metros with high-bandwidth backbone trunks between.
SMB Accessible
The sophistication of modern backup solutions is often considered to be “enterprise-only,” and so midsize businesses often opt for VMs, but the reality is that 75 % of SMBs, if hit by ransomware, would be forced to cease operations due to the devastation of downtime. The price of a midrange server lease at Melbicom is worth every penny, providing a single dedicated backup server in a secondary site through block-level replication of data secured with high-level encryption brings peace of mind. There is no throttling, and recoveries run locally at LAN speed, and automation is especially beneficial to smaller operations with limited IT teams.
Geography, Speed, and Automation: Make the Most of Every Minute
Current downtime trend statistics all signal that outages are costlier, attackers are quicker, and customer tolerance is lower. Thankfully, by geographically separating production and standby services like we do here at Melbicom, you have the cornerstone of a defensive blueprint. Securing operations requires block-level, encrypted replication for near-perfect sync. Data streams then need compression and WAN acceleration, seeding the first copy offline, and scripting the spin-ups. That way, you have a failover that is integrated into daily workflows. Executing this defense blueprint slashes an enterprise’s RTO to minutes and ensures that even the most catastrophic outage is merely a blip.
Get Your Backup-Ready Server
Deploy a dedicated server in any of 21 Tier III/IV locations and achieve minutes-level disaster recovery.